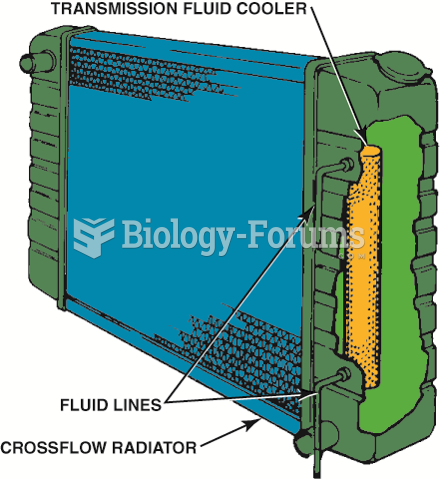
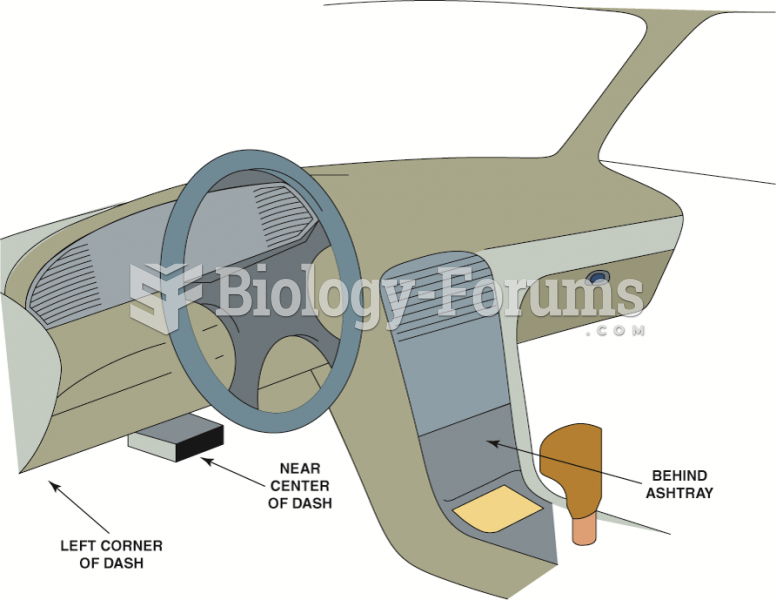
|
|
|
The most dangerous mercury compound, dimethyl mercury, is so toxic that even a few microliters spilled on the skin can cause death. Mercury has been shown to accumulate in higher amounts in the following types of fish than other types: swordfish, shark, mackerel, tilefish, crab, and tuna.
More than nineteen million Americans carry the factor V gene that causes blood clots, pulmonary embolism, and heart disease.
Coca-Cola originally used coca leaves and caffeine from the African kola nut. It was advertised as a therapeutic agent and "pickerupper." Eventually, its formulation was changed, and the coca leaves were removed because of the effects of regulation on cocaine-related products.
There are more sensory neurons in the tongue than in any other part of the body.
HIV testing reach is still limited. An estimated 40% of people with HIV (more than 14 million) remain undiagnosed and do not know their infection status.