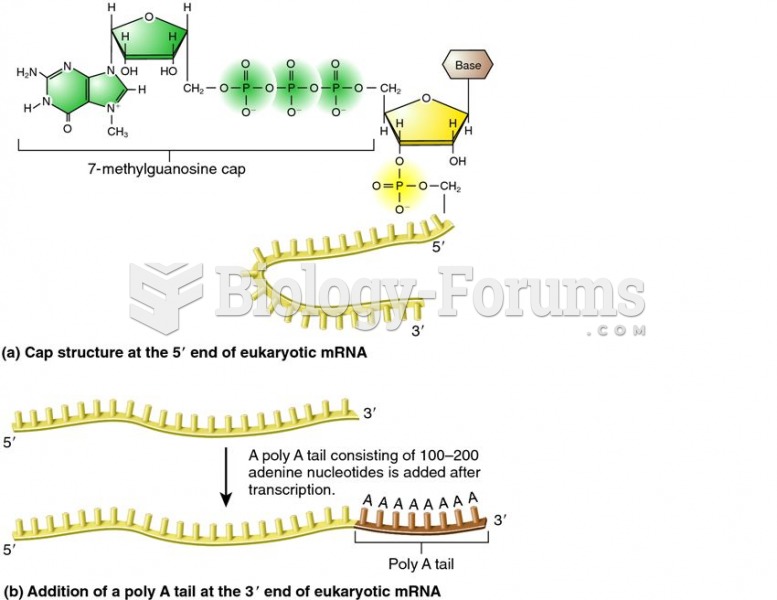
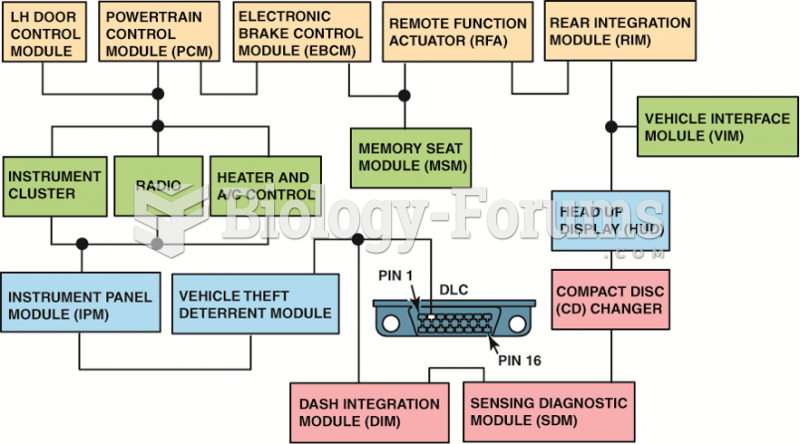
|
|
|
When intravenous medications are involved in adverse drug events, their harmful effects may occur more rapidly, and be more severe than errors with oral medications. This is due to the direct administration into the bloodstream.
Egg cells are about the size of a grain of sand. They are formed inside of a female's ovaries before she is even born.
The effects of organophosphate poisoning are referred to by using the abbreviations “SLUD” or “SLUDGE,” It stands for: salivation, lacrimation, urination, defecation, GI upset, and emesis.
Critical care patients are twice as likely to receive the wrong medication. Of these errors, 20% are life-threatening, and 42% require additional life-sustaining treatments.
Computer programs are available that crosscheck a new drug's possible trade name with all other trade names currently available. These programs detect dangerous similarities between names and alert the manufacturer of the drug.