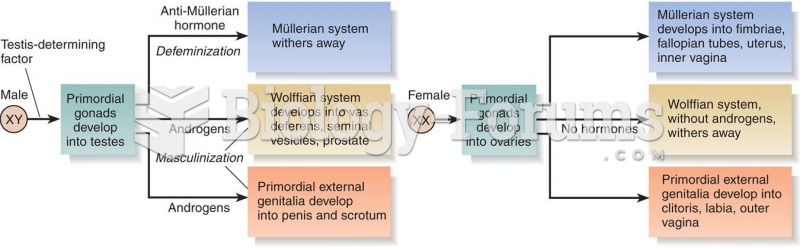
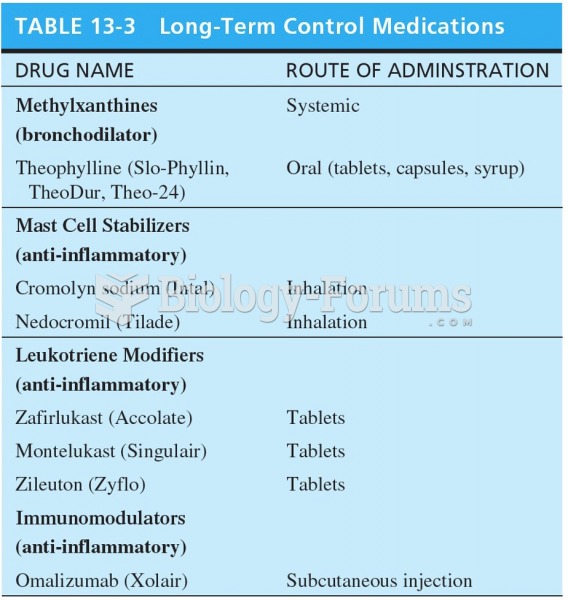
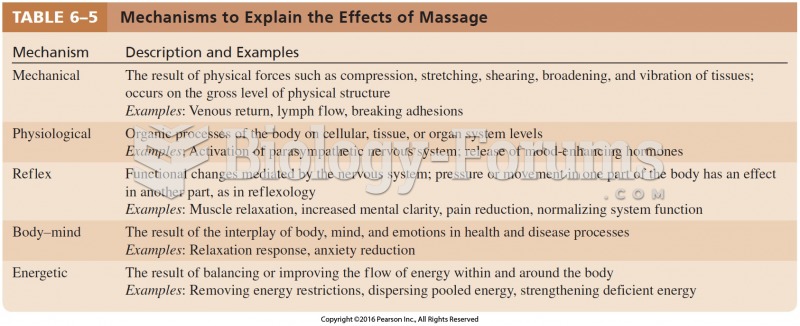
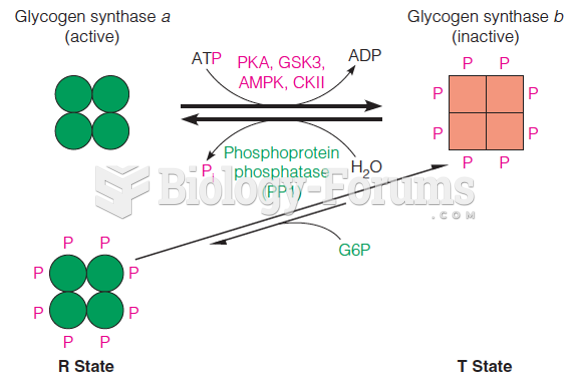
|
|
|
Blastomycosis is often misdiagnosed, resulting in tragic outcomes. It is caused by a fungus living in moist soil, in wooded areas of the United States and Canada. If inhaled, the fungus can cause mild breathing problems that may worsen and cause serious illness and even death.
Only one in 10 cancer deaths is caused by the primary tumor. The vast majority of cancer mortality is caused by cells breaking away from the main tumor and metastasizing to other parts of the body, such as the brain, bones, or liver.
Asthma attacks and symptoms usually get started by specific triggers (such as viruses, allergies, gases, and air particles). You should talk to your doctor about these triggers and find ways to avoid or get rid of them.
Cocaine was isolated in 1860 and first used as a local anesthetic in 1884. Its first clinical use was by Sigmund Freud to wean a patient from morphine addiction. The fictional character Sherlock Holmes was supposed to be addicted to cocaine by injection.
Oliver Wendell Holmes is credited with introducing the words "anesthesia" and "anesthetic" into the English language in 1846.