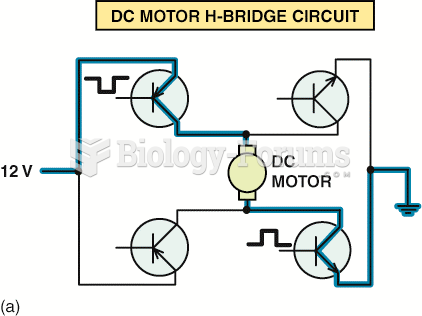
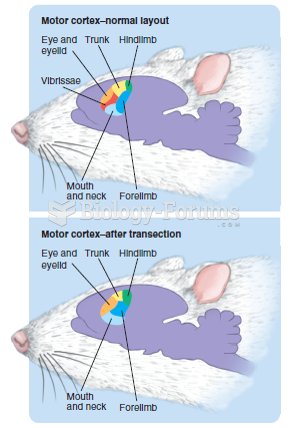
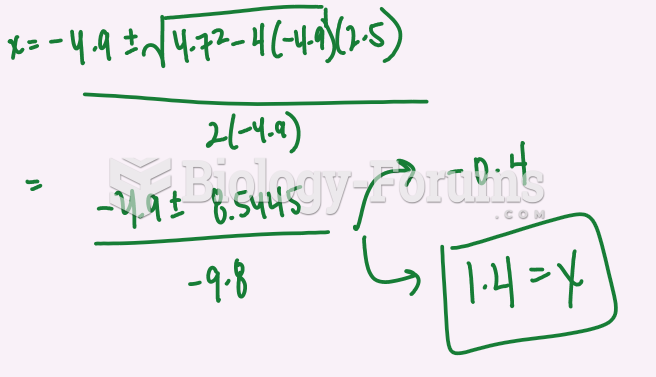|
|
|
Multiple sclerosis is a condition wherein the body's nervous system is weakened by an autoimmune reaction that attacks the myelin sheaths of neurons.
Walt Disney helped combat malaria by making an animated film in 1943 called The Winged Scourge. This short film starred the seven dwarfs and taught children that mosquitos transmit malaria, which is a very bad disease. It advocated the killing of mosquitos to stop the disease.
Oxytocin is recommended only for pregnancies that have a medical reason for inducing labor (such as eclampsia) and is not recommended for elective procedures or for making the birthing process more convenient.
Sildenafil (Viagra®) has two actions that may be of consequence in patients with heart disease. It can lower the blood pressure, and it can interact with nitrates. It should never be used in patients who are taking nitrates.
There are actually 60 minerals, 16 vitamins, 12 essential amino acids, and three essential fatty acids that your body needs every day.