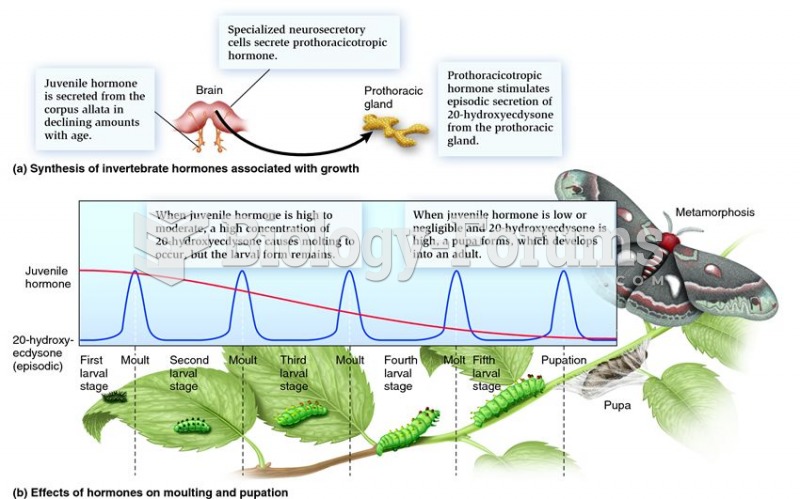
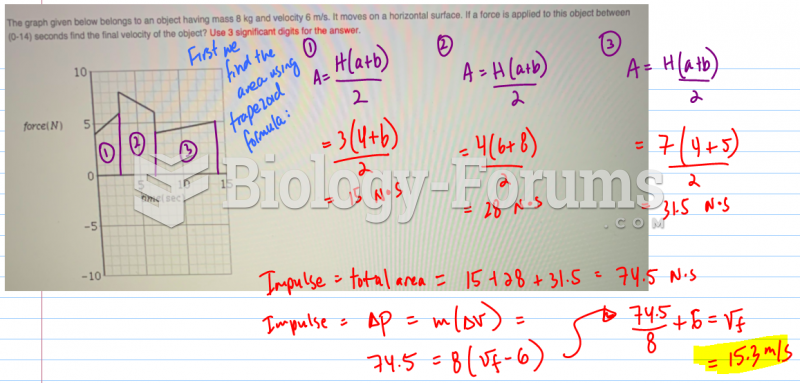
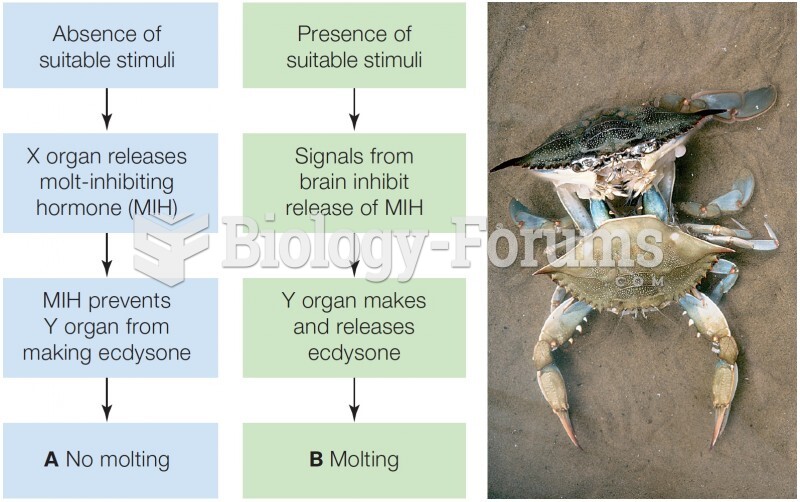
|
|
|
Illness; diuretics; laxative abuse; hot weather; exercise; sweating; caffeine; alcoholic beverages; starvation diets; inadequate carbohydrate consumption; and diets high in protein, salt, or fiber can cause people to become dehydrated.
Hip fractures are the most serious consequences of osteoporosis. The incidence of hip fractures increases with each decade among patients in their 60s to patients in their 90s for both women and men of all populations. Men and women older than 80 years of age show the highest incidence of hip fractures.
When Gabriel Fahrenheit invented the first mercury thermometer, he called "zero degrees" the lowest temperature he was able to attain with a mixture of ice and salt. For the upper point of his scale, he used 96°, which he measured as normal human body temperature (we know it to be 98.6° today because of more accurate thermometers).
Cytomegalovirus affects nearly the same amount of newborns every year as Down syndrome.
The first oncogene was discovered in 1970 and was termed SRC (pronounced "SARK").