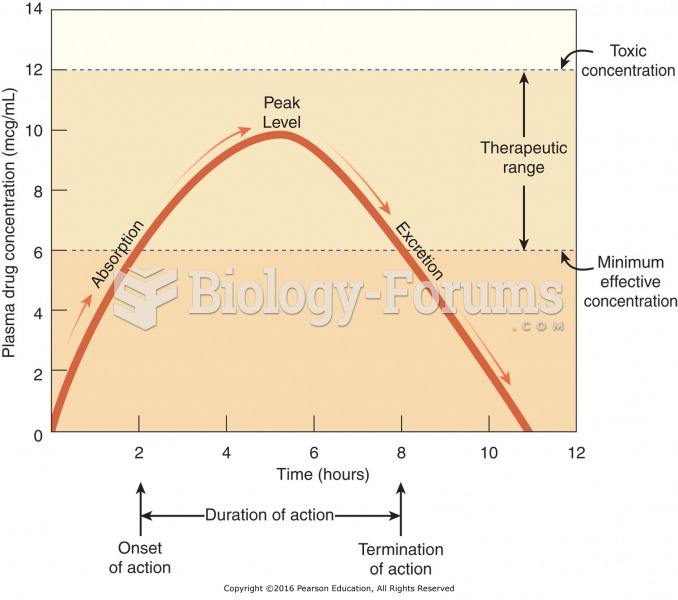
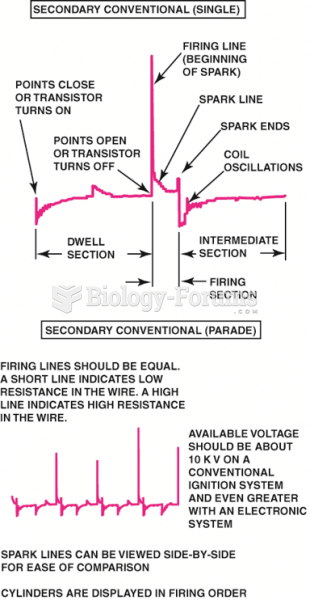
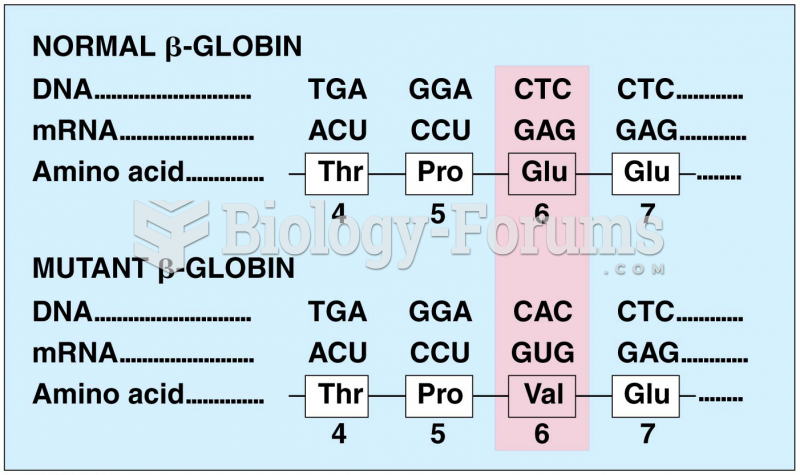
|
|
|
The top 10 most important tips that will help you grow old gracefully include (1) quit smoking, (2) keep your weight down, (3) take supplements, (4) skip a meal each day or fast 1 day per week, (5) get a pet, (6) get medical help for chronic pain, (7) walk regularly, (8) reduce arguments, (9) put live plants in your living space, and (10) do some weight training.
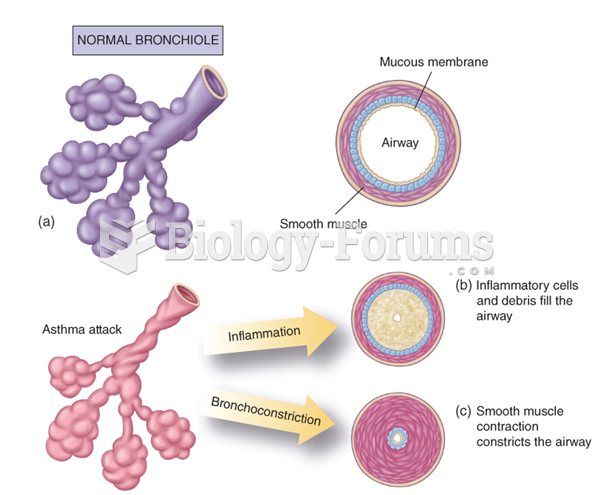
Asthma is the most common chronic childhood disease in the world. Most children who develop asthma have symptoms before they are 5 years old.
The ratio of hydrogen atoms to oxygen in water (H2O) is 2:1.
The first oral chemotherapy drug for colon cancer was approved by FDA in 2001.
Pope Sylvester II tried to introduce Arabic numbers into Europe between the years 999 and 1003, but their use did not catch on for a few more centuries, and Roman numerals continued to be the primary number system.