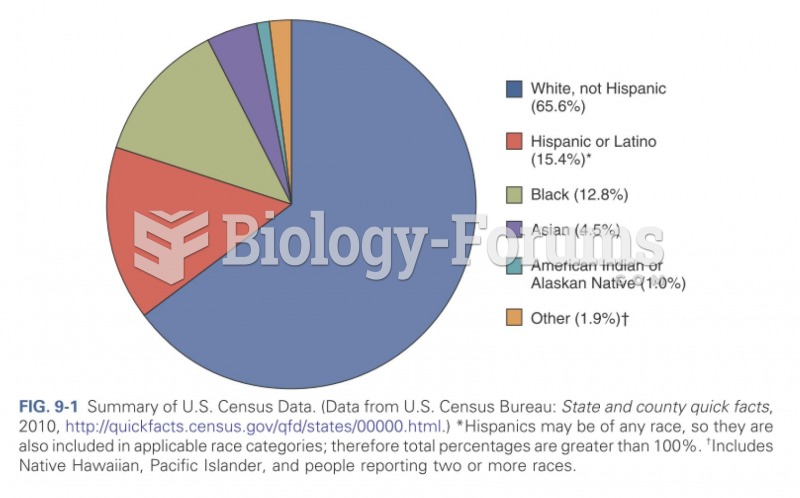
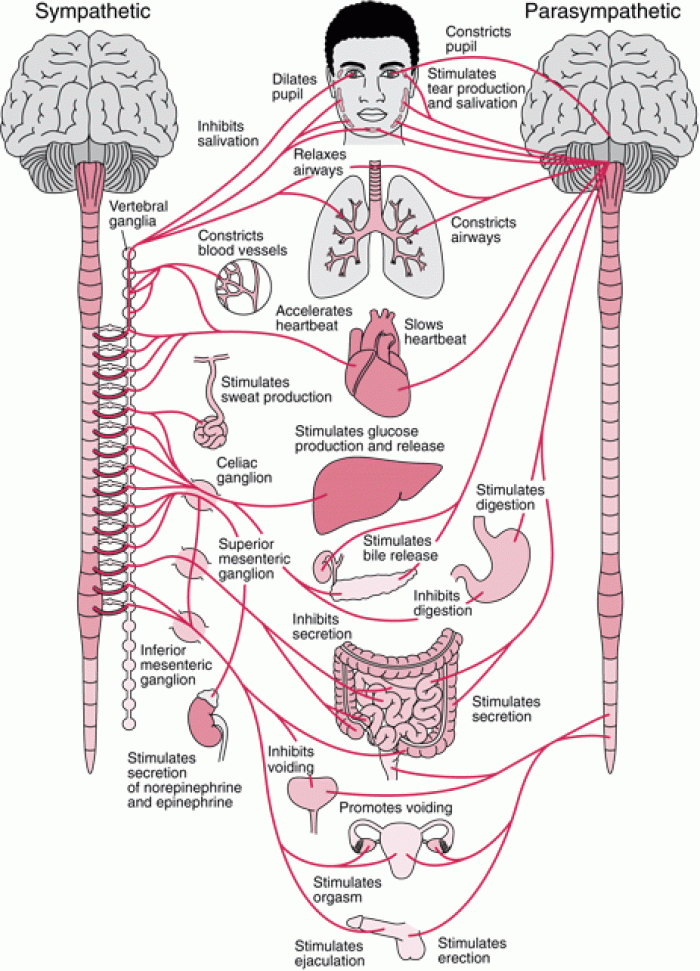
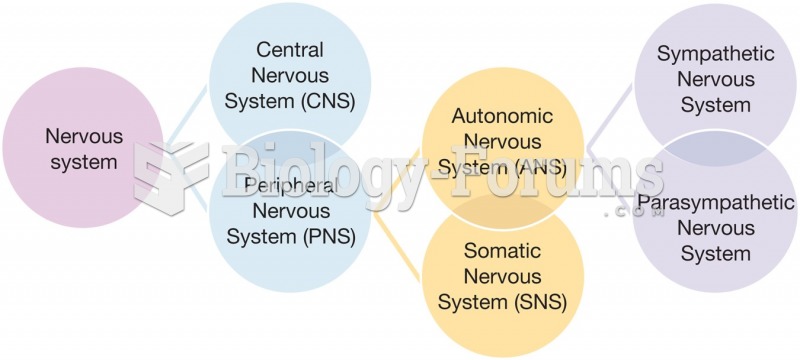
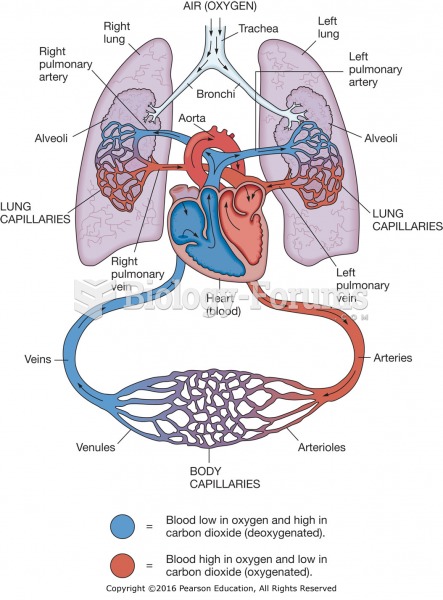
|
|
|
Acetaminophen (Tylenol) in overdose can seriously damage the liver. It should never be taken by people who use alcohol heavily; it can result in severe liver damage and even a condition requiring a liver transplant.
Chronic marijuana use can damage the white blood cells and reduce the immune system's ability to respond to disease by as much as 40%. Without a strong immune system, the body is vulnerable to all kinds of degenerative and infectious diseases.
Pope Sylvester II tried to introduce Arabic numbers into Europe between the years 999 and 1003, but their use did not catch on for a few more centuries, and Roman numerals continued to be the primary number system.
If you use artificial sweeteners, such as cyclamates, your eyes may be more sensitive to light. Other factors that will make your eyes more sensitive to light include use of antibiotics, oral contraceptives, hypertension medications, diuretics, and antidiabetic medications.
Bacteria have flourished on the earth for over three billion years. They were the first life forms on the planet.