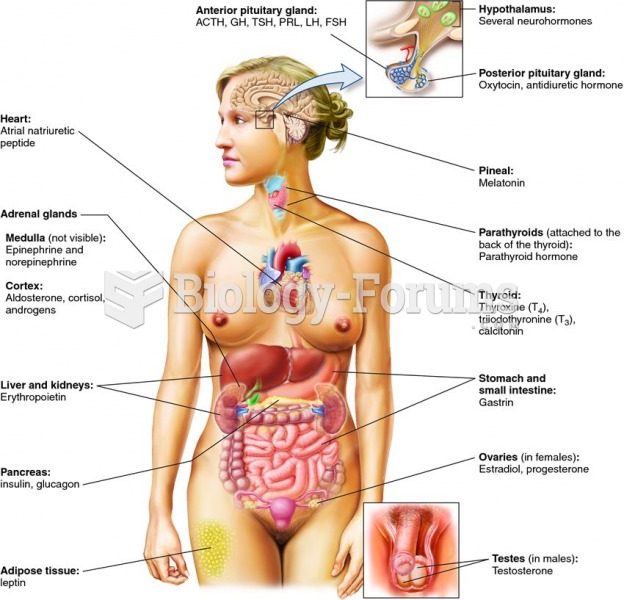
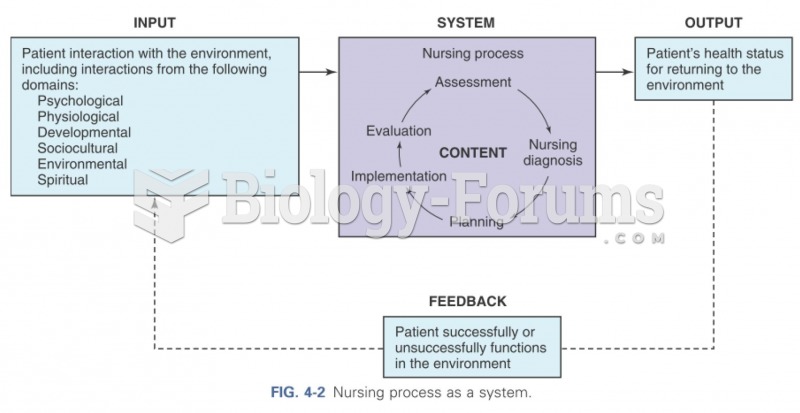
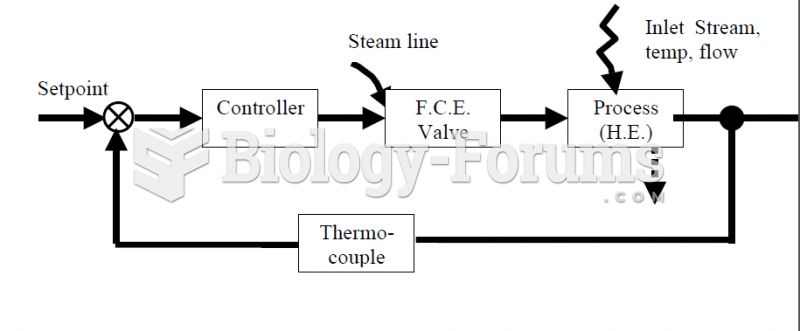
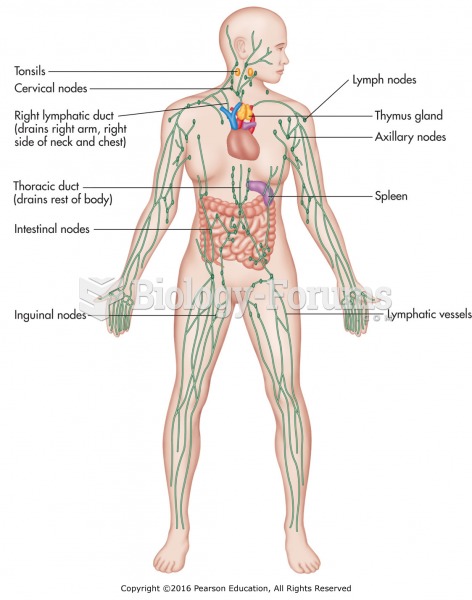
|
|
|
Inotropic therapy does not have a role in the treatment of most heart failure patients. These drugs can make patients feel and function better but usually do not lengthen the predicted length of their lives.
There are more bacteria in your mouth than there are people in the world.
The U.S. Pharmacopeia Medication Errors Reporting Program states that approximately 50% of all medication errors involve insulin.
Liver spots have nothing whatsoever to do with the liver. They are a type of freckles commonly seen in older adults who have been out in the sun without sufficient sunscreen.
Patients who have been on total parenteral nutrition for more than a few days may need to have foods gradually reintroduced to give the digestive tract time to start working again.