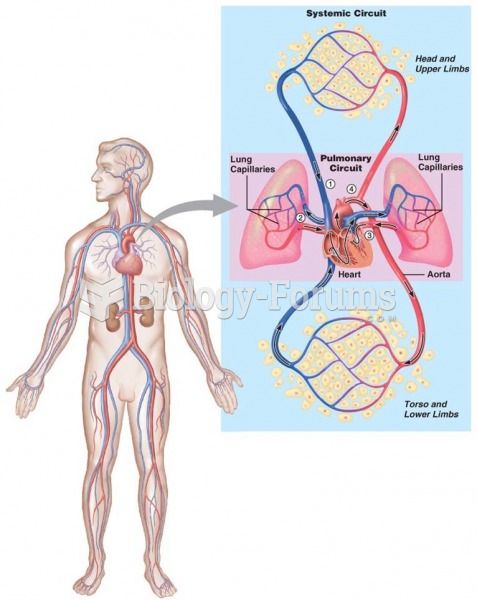
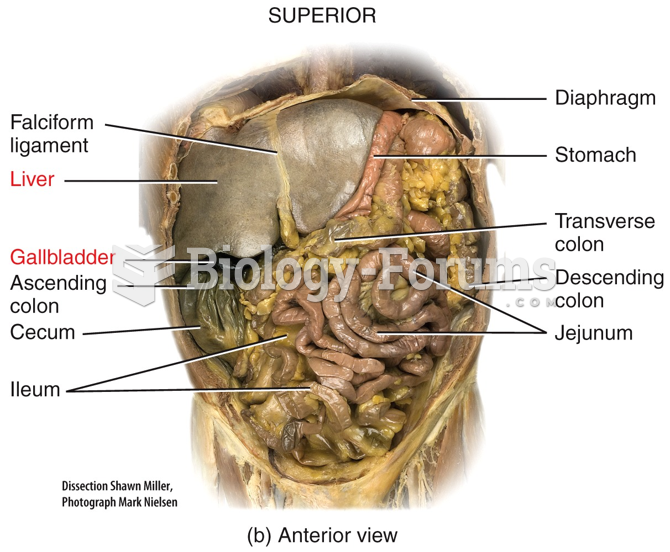
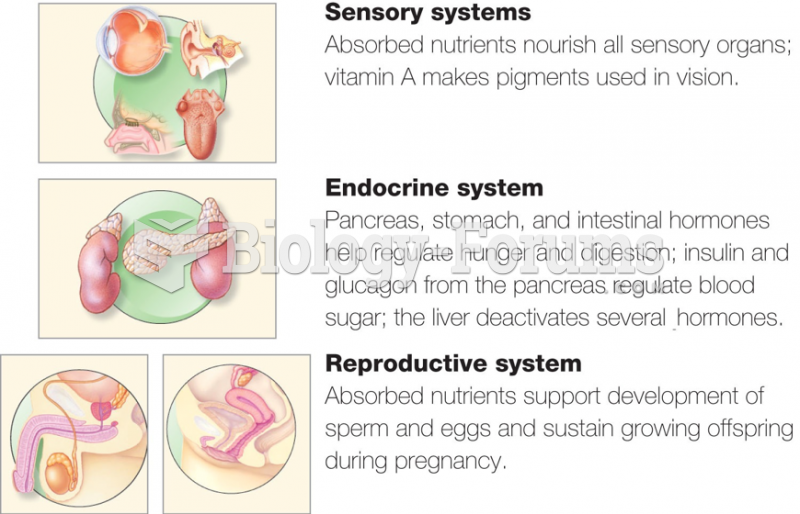
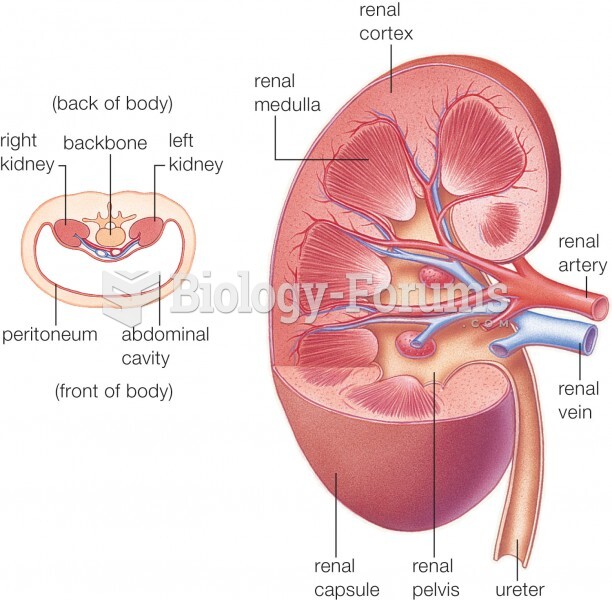
|
|
|
Signs and symptoms that may signify an eye tumor include general blurred vision, bulging eye(s), double vision, a sensation of a foreign body in the eye(s), iris defects, limited ability to move the eyelid(s), limited ability to move the eye(s), pain or discomfort in or around the eyes or eyelids, red or pink eyes, white or cloud spots on the eye(s), colored spots on the eyelid(s), swelling around the eyes, swollen eyelid(s), and general vision loss.
It is widely believed that giving a daily oral dose of aspirin to heart attack patients improves their chances of survival because the aspirin blocks the formation of new blood clots.
Though methadone is often used to treat dependency on other opioids, the drug itself can be abused. Crushing or snorting methadone can achieve the opiate "rush" desired by addicts. Improper use such as these can lead to a dangerous dependency on methadone. This drug now accounts for nearly one-third of opioid-related deaths.
The strongest synthetic topical retinoid drug available, tazarotene, is used to treat sun-damaged skin, acne, and psoriasis.
The newest statin drug, rosuvastatin, has been called a superstatin because it appears to reduce LDL cholesterol to a greater degree than the other approved statin drugs.