|
|
|
Glaucoma is a leading cause of blindness. As of yet, there is no cure. Everyone is at risk, and there may be no warning signs. It is six to eight times more common in African Americans than in whites. The best and most effective way to detect glaucoma is to receive a dilated eye examination.
Liver spots have nothing whatsoever to do with the liver. They are a type of freckles commonly seen in older adults who have been out in the sun without sufficient sunscreen.
In the United States, an estimated 50 million unnecessary antibiotics are prescribed for viral respiratory infections.
The word drug comes from the Dutch word droog (meaning "dry"). For centuries, most drugs came from dried plants, hence the name.
Sildenafil (Viagra®) has two actions that may be of consequence in patients with heart disease. It can lower the blood pressure, and it can interact with nitrates. It should never be used in patients who are taking nitrates.
 A pygmy hippopotamus rests in some water to help prevent its skin from cracking at Ueno Zoo in Japan
A pygmy hippopotamus rests in some water to help prevent its skin from cracking at Ueno Zoo in Japan
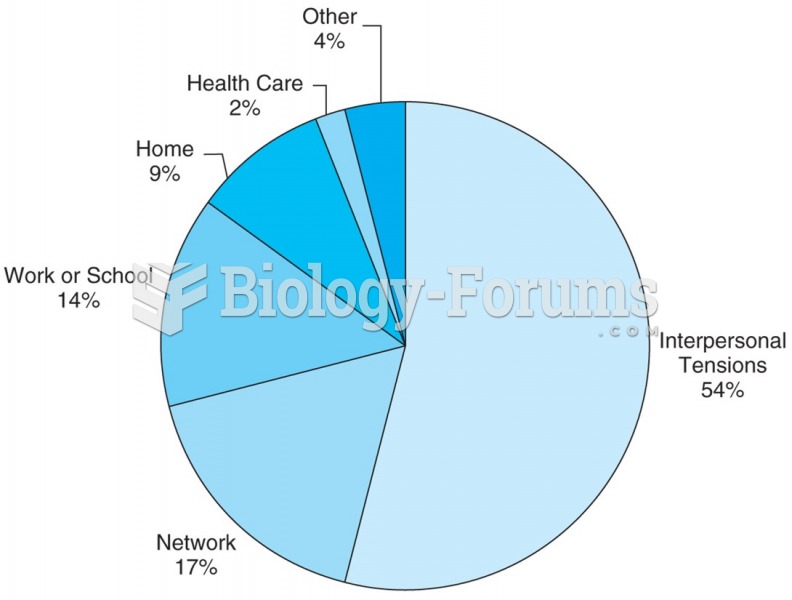 U.S. adults from 25 to 74 years report that the largest proportion of their daily stressors arise ...
U.S. adults from 25 to 74 years report that the largest proportion of their daily stressors arise ...