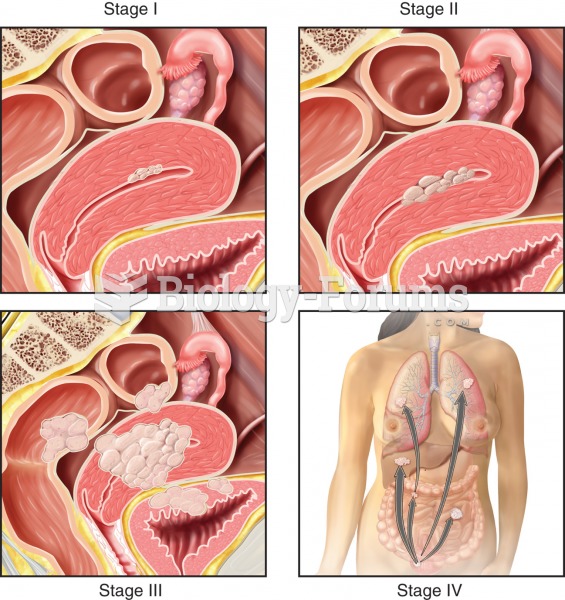
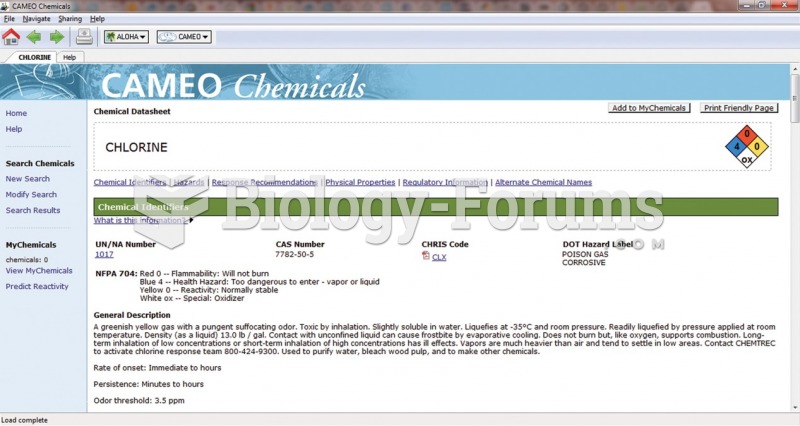
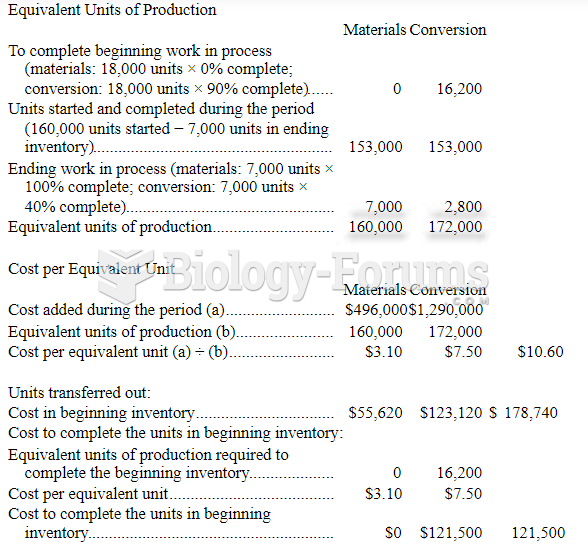
|
|
|
Since 1988, the CDC has reported a 99% reduction in bacterial meningitis caused by Haemophilus influenzae, due to the introduction of the vaccine against it.
Amoebae are the simplest type of protozoans, and are characterized by a feeding and dividing trophozoite stage that moves by temporary extensions called pseudopodia or false feet.
Thyroid conditions cause a higher risk of fibromyalgia and chronic fatigue syndrome.
Eating carrots will improve your eyesight. Carrots are high in vitamin A (retinol), which is essential for good vision. It can also be found in milk, cheese, egg yolks, and liver.
Vital signs (blood pressure, temperature, pulse rate, respiration rate) should be taken before any drug administration. Patients should be informed not to use tobacco or caffeine at least 30 minutes before their appointment.