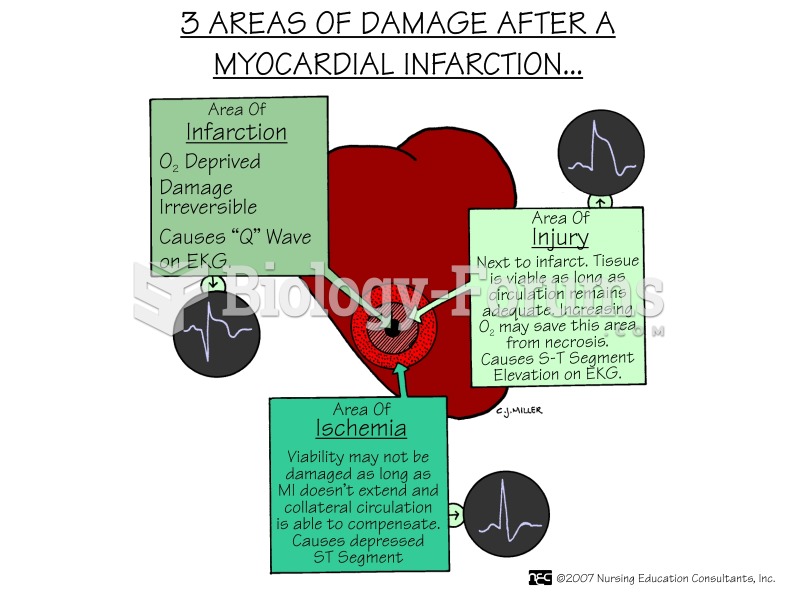
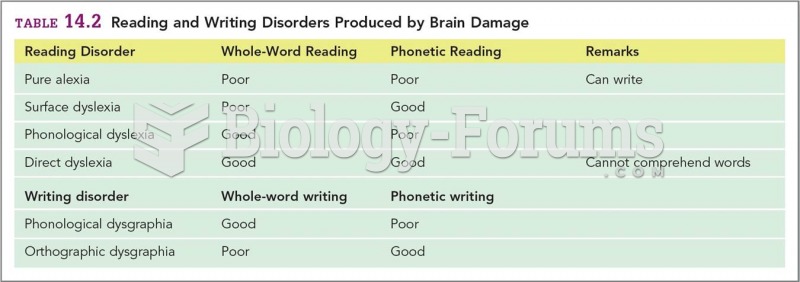
Answer to Question 1
A zombie is a Trojan horse that secretly takes over another computer for the purpose of launching attacks on other computers. The computers running the zombie are also sometimes called zombies.
When a Trojan horse (or other type of virus) has taken over a large number of computers (and thus made them into zombies), the person who planted the virus can take control of all the computers and form a botnet (short for robotic network, also called a zombie farm when the computers in the network are zombies) that can act as an attacking unit, sending spam or launching denial-of-service attacks against specific Web sites.
Answer to Question 2
Java adds functionality to business applications and can handle transactions and a wide variety of actions on a client computer. This relieves an otherwise busy server-side program from handling thousands of transactions simultaneously. Once downloaded however, embedded Java code can run on a clients computer and cause damage, run a Trojan horse, or turn the computer into a zombie.
To counter this threat, the Java sandbox security model was developed. The Java sandbox confines Java applet actions to a set of rules defined by the security model.
These rules apply to all untrusted Java applets. Untrusted Java applets are those that have not been established as secure. When Java applets are run within the constraints of the sandbox, they do not have full access to the client computer.