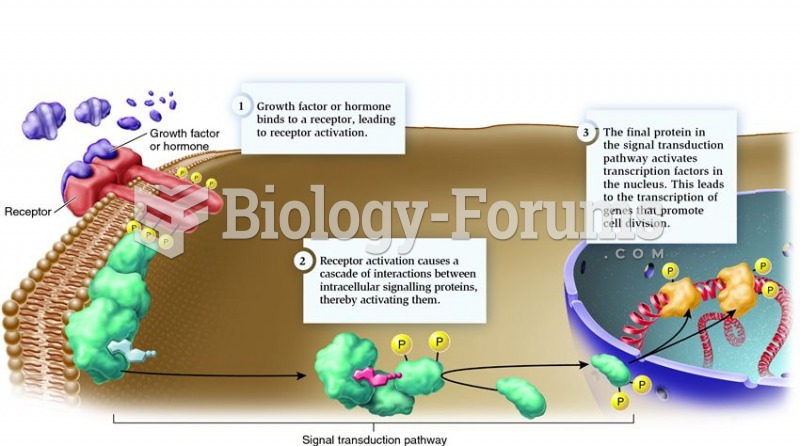
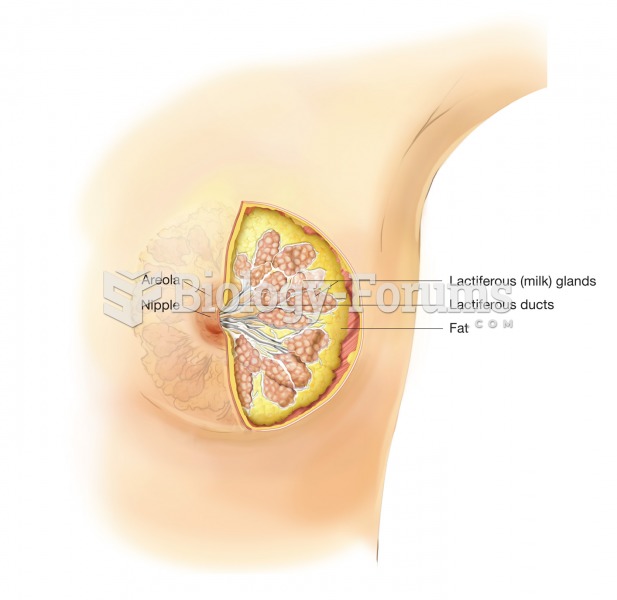
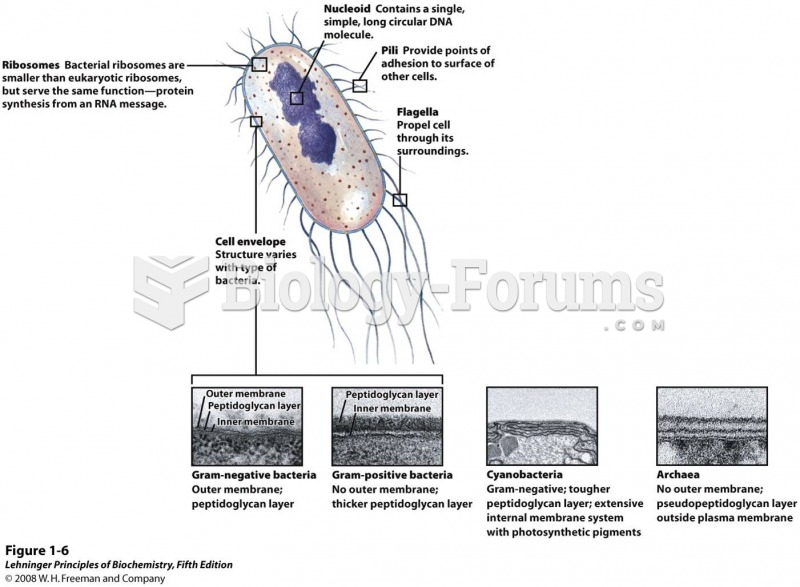
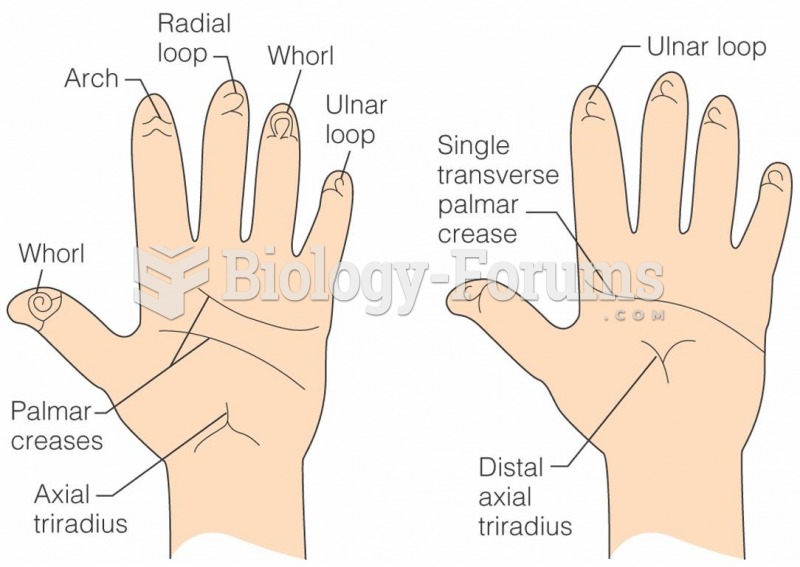
|
|
|
Every flu season is different, and even healthy people can get extremely sick from the flu, as well as spread it to others. The flu season can begin as early as October and last as late as May. Every person over six months of age should get an annual flu vaccine. The vaccine cannot cause you to get influenza, but in some seasons, may not be completely able to prevent you from acquiring influenza due to changes in causative viruses. The viruses in the flu shot are killed—there is no way they can give you the flu. Minor side effects include soreness, redness, or swelling where the shot was given. It is possible to develop a slight fever, and body aches, but these are simply signs that the body is responding to the vaccine and making itself ready to fight off the influenza virus should you come in contact with it.
There used to be a metric calendar, as well as metric clocks. The metric calendar, or "French Republican Calendar" divided the year into 12 months, but each month was divided into three 10-day weeks. Each day had 10 decimal hours. Each hour had 100 decimal minutes. Due to lack of popularity, the metric clocks and calendars were ended in 1795, three years after they had been first marketed.
The average adult has about 21 square feet of skin.
During pregnancy, a woman is more likely to experience bleeding gums and nosebleeds caused by hormonal changes that increase blood flow to the mouth and nose.
In 2006, a generic antinausea drug named ondansetron was approved. It is used to stop nausea and vomiting associated with surgery, chemotherapy, and radiation therapy.