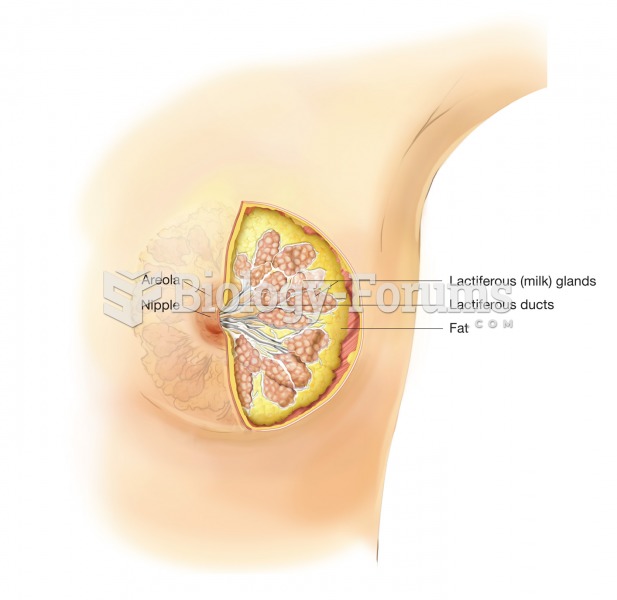
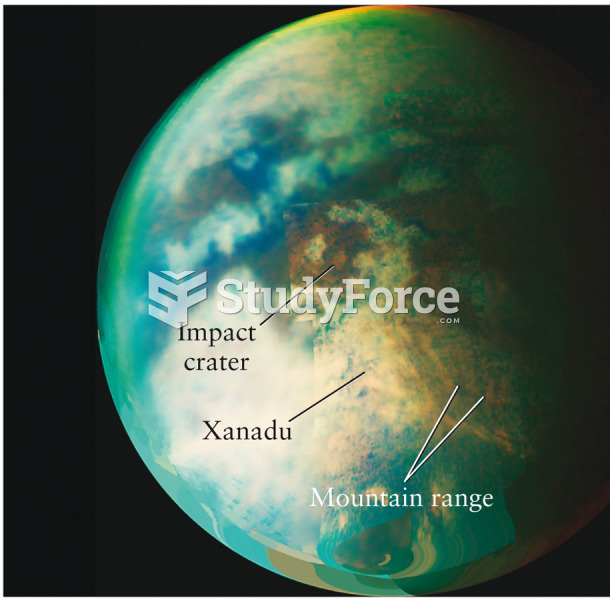
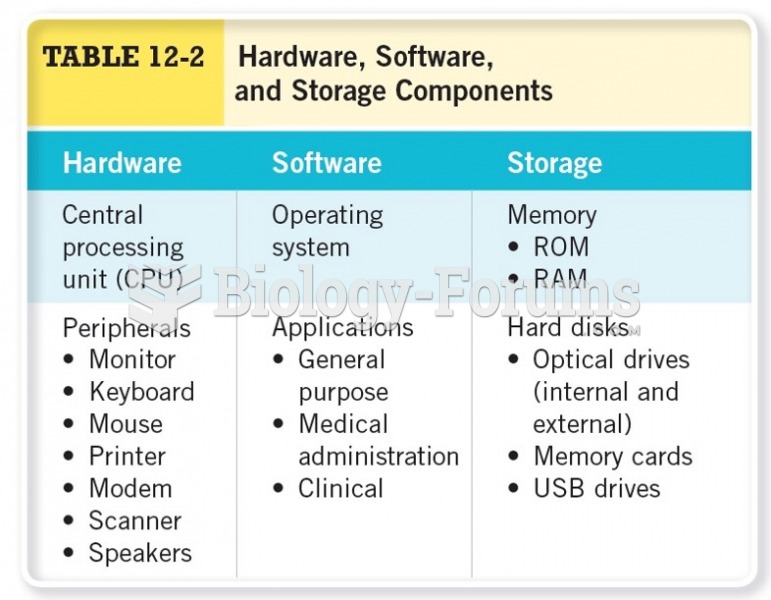
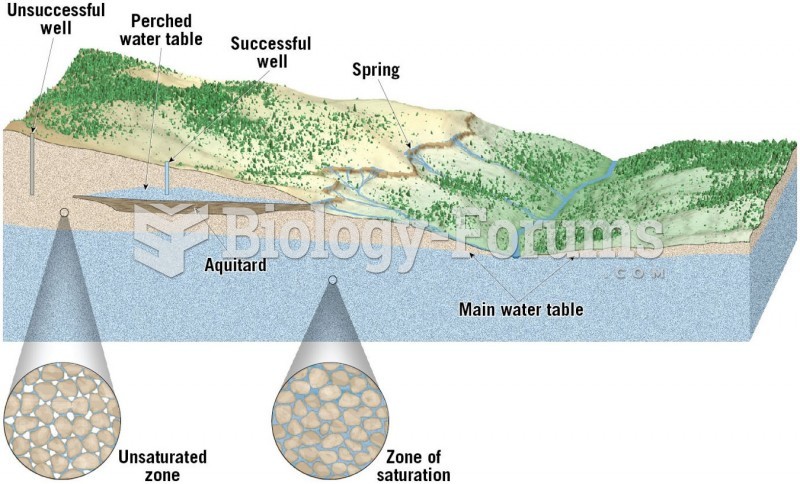
Answer to Question 1
Project- and issue-tracking software offers useful features to help developers stay abreast of all aspects of their projects. Developers can upload diagrams and documentation, comment on activity, describe challenges, report bugs, and request assistance. The software maintains a complete history of project activity, including dates showing when each module was started and completed and who has been assigned each task. It also offers customizable dashboards so developers can see at a glance how the project is coming along and which activities they need to complete today.
Answer to Question 2
Wireless networks are vulnerable because radio frequency bands are easy to scan. Both Bluetooth and Wi-Fi networks are susceptible to hacking by eavesdroppers. Local area networks (LANs) using the 802.11 standard can be easily penetrated by outsiders armed with laptops, wireless cards, external antennae, and hacking software. Hackers use these tools to detect unprotected networks, monitor network traffic, and, in some cases, gain access to the Internet or to corporate networks. Wi-Fi transmission technology was designed to make it easy for stations to find and hear one another. The service set identifiers (SSIDs) identifying the access points in a Wi-Fi network are broadcast multiple times and can be picked up fairly easily by intruders' sniffer programs. Wireless networks in many locations do not have basic protections against war driving, in which eavesdroppers drive by buildings or park outside and try to intercept wireless network traffic. A hacker can employ an 802.11 analysis tool to identify the SSID. An intruder that has associated with an access point by using the correct SSID is capable of accessing other resources on the network, using the Windows operating system to determine which other users are connected to the network, access their computer hard drives, and open or copy their files. Intruders also use the information they have gleaned to set up rogue access points on a different radio channel in physical locations close to users to force a user's radio NIC to associate with the rogue access point. Once this association occurs, hackers using the rogue access point can capture the names and passwords of unsuspecting users.