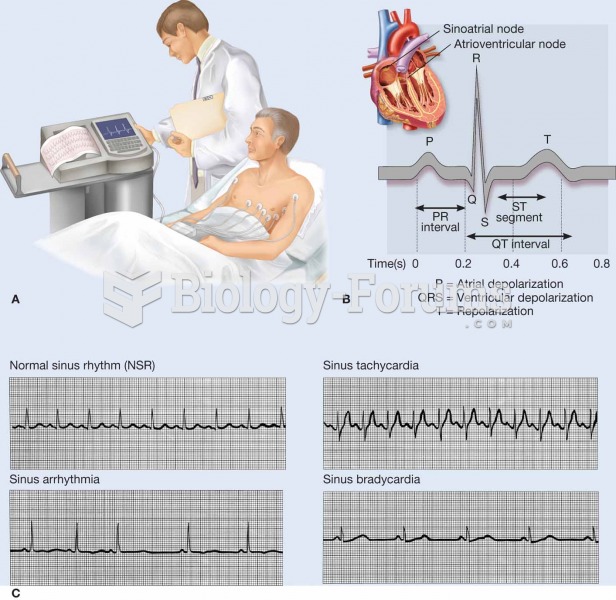
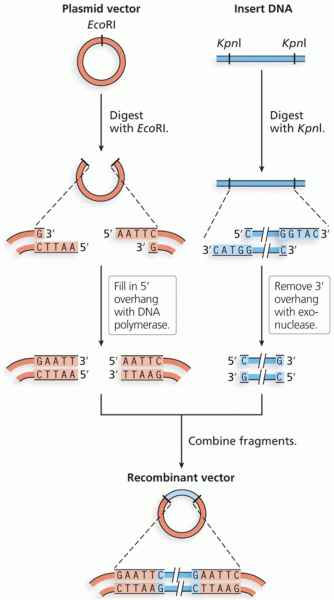
|
|
|
Acetaminophen (Tylenol) in overdose can seriously damage the liver. It should never be taken by people who use alcohol heavily; it can result in severe liver damage and even a condition requiring a liver transplant.
Anesthesia awareness is a potentially disturbing adverse effect wherein patients who have been paralyzed with muscle relaxants may awaken. They may be aware of their surroundings but unable to communicate or move. Neurologic monitoring equipment that helps to more closely check the patient's anesthesia stages is now available to avoid the occurrence of anesthesia awareness.
Walt Disney helped combat malaria by making an animated film in 1943 called The Winged Scourge. This short film starred the seven dwarfs and taught children that mosquitos transmit malaria, which is a very bad disease. It advocated the killing of mosquitos to stop the disease.
Famous people who died from poisoning or drug overdose include, Adolf Hitler, Socrates, Juan Ponce de Leon, Marilyn Monroe, Judy Garland, and John Belushi.
The senior population grows every year. Seniors older than 65 years of age now comprise more than 13% of the total population. However, women outlive men. In the 85-and-over age group, there are only 45 men to every 100 women.