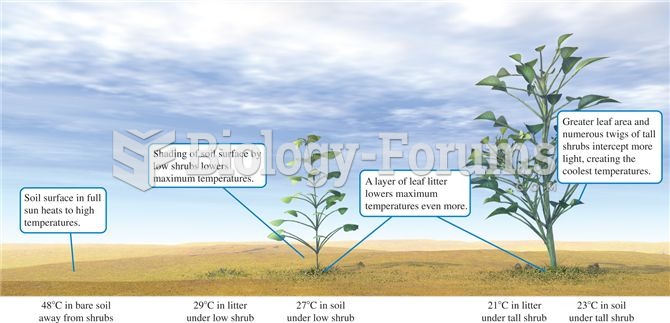
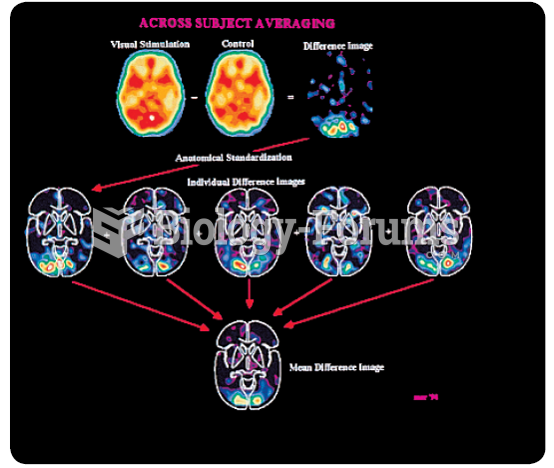
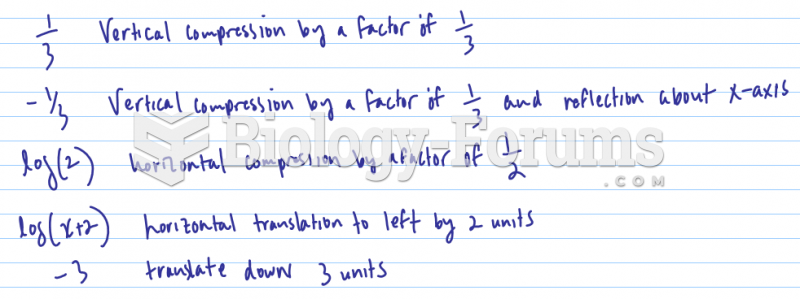
|
|
|
The Food and Drug Administration has approved Risperdal, an adult antipsychotic drug, for the symptomatic treatment of irritability in children and adolescents with autism. The approval is the first for the use of a drug to treat behaviors associated with autism in children. These behaviors are included under the general heading of irritability and include aggression, deliberate self-injury, and temper tantrums.
Egg cells are about the size of a grain of sand. They are formed inside of a female's ovaries before she is even born.
Nearly 31 million adults in America have a total cholesterol level that is more than 240 mg per dL.
The average older adult in the United States takes five prescription drugs per day. Half of these drugs contain a sedative. Alcohol should therefore be avoided by most senior citizens because of the dangerous interactions between alcohol and sedatives.
In the United States, congenital cytomegalovirus causes one child to become disabled almost every hour. CMV is the leading preventable viral cause of development disability in newborns. These disabilities include hearing or vision loss, and cerebral palsy.
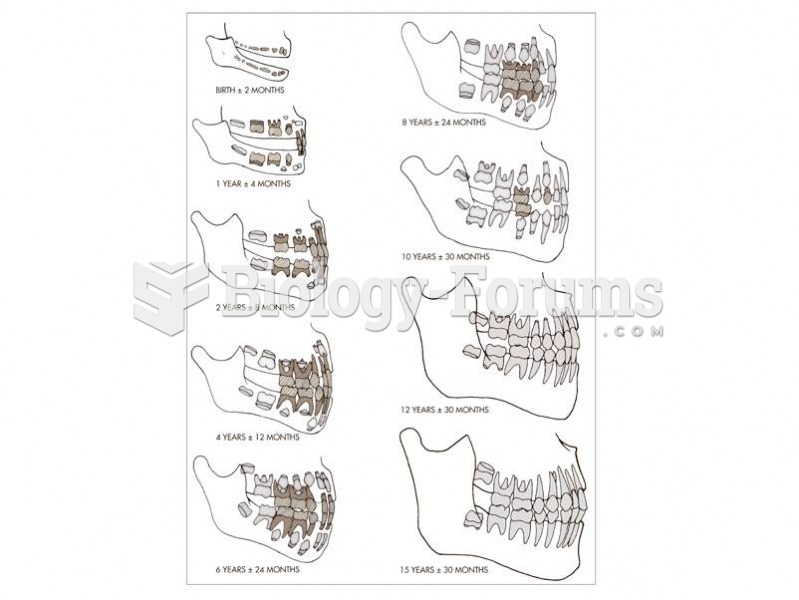 Tooth development and eruption are commonly used to assess age in the subadult skeleton. Deciduous (
Tooth development and eruption are commonly used to assess age in the subadult skeleton. Deciduous (
 The philosophical journey requires self-examination. Your responsibility as a critical thinker is to
The philosophical journey requires self-examination. Your responsibility as a critical thinker is to