|
|
|
If all the neurons in the human body were lined up, they would stretch more than 600 miles.
In inpatient settings, adverse drug events account for an estimated one in three of all hospital adverse events. They affect approximately 2 million hospital stays every year, and prolong hospital stays by between one and five days.
Asthma cases in Americans are about 75% higher today than they were in 1980.
The first monoclonal antibodies were made exclusively from mouse cells. Some are now fully human, which means they are likely to be safer and may be more effective than older monoclonal antibodies.
Pope Sylvester II tried to introduce Arabic numbers into Europe between the years 999 and 1003, but their use did not catch on for a few more centuries, and Roman numerals continued to be the primary number system.
 Does this child have legs of different lengths or scoliosis? Look at the level of the iliac crests a
Does this child have legs of different lengths or scoliosis? Look at the level of the iliac crests a
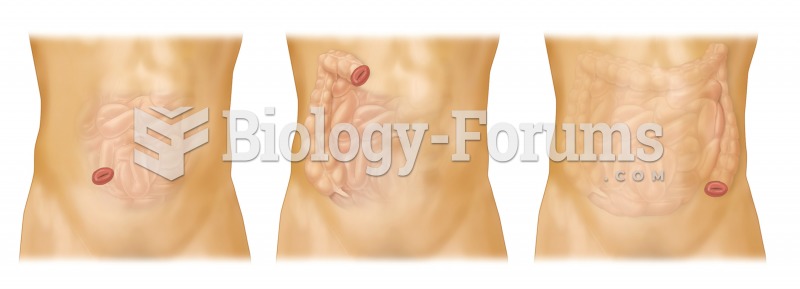 Colostomy. Alternate versions of colostomy are illustrated, each of which creates one or more new op
Colostomy. Alternate versions of colostomy are illustrated, each of which creates one or more new op
 A portable mercury sphygmomanometer. Mercury versions are being phased out of medical offices and ...
A portable mercury sphygmomanometer. Mercury versions are being phased out of medical offices and ...