|
|
|
All adverse reactions are commonly charted in red ink in the patient's record and usually are noted on the front of the chart. Failure to follow correct documentation procedures may result in malpractice lawsuits.
Acetaminophen (Tylenol) in overdose can seriously damage the liver. It should never be taken by people who use alcohol heavily; it can result in severe liver damage and even a condition requiring a liver transplant.
The immune system needs 9.5 hours of sleep in total darkness to recharge completely.
Medications that are definitely not safe to take when breastfeeding include radioactive drugs, antimetabolites, some cancer (chemotherapy) agents, bromocriptine, ergotamine, methotrexate, and cyclosporine.
More than 150,000 Americans killed by cardiovascular disease are younger than the age of 65 years.
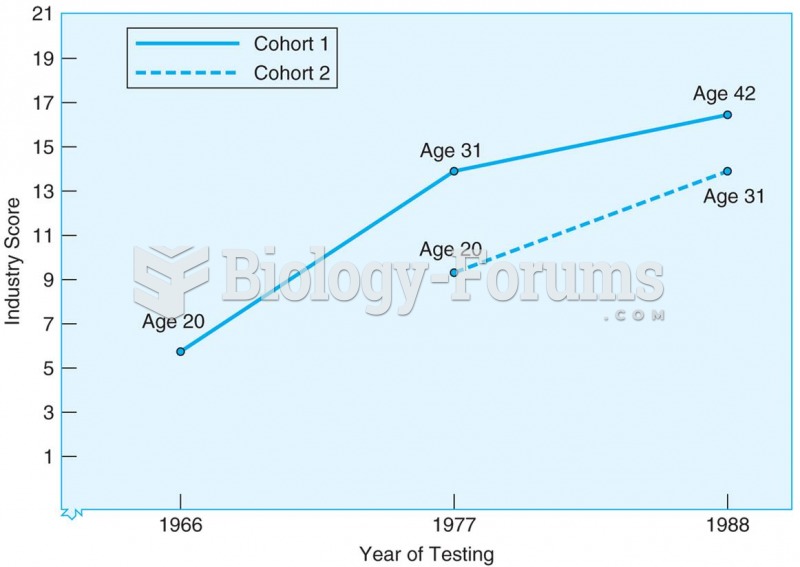 Results from sequential study of two cohorts tested at three ages and at three different points in t
Results from sequential study of two cohorts tested at three ages and at three different points in t
 The gaping hole in the destroyer USS Cole, in the port of Aden, Yemen, was the work of suicide bombe
The gaping hole in the destroyer USS Cole, in the port of Aden, Yemen, was the work of suicide bombe





