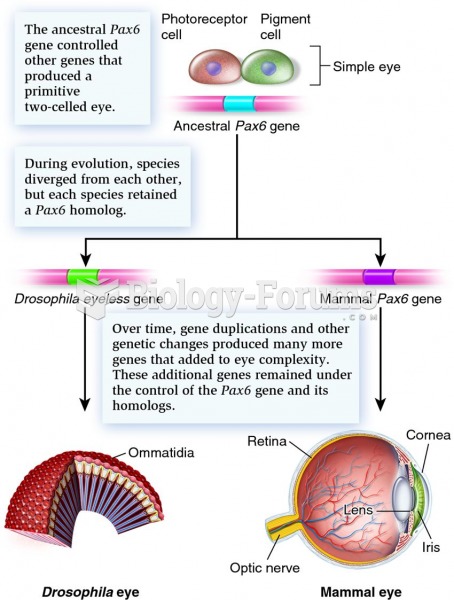
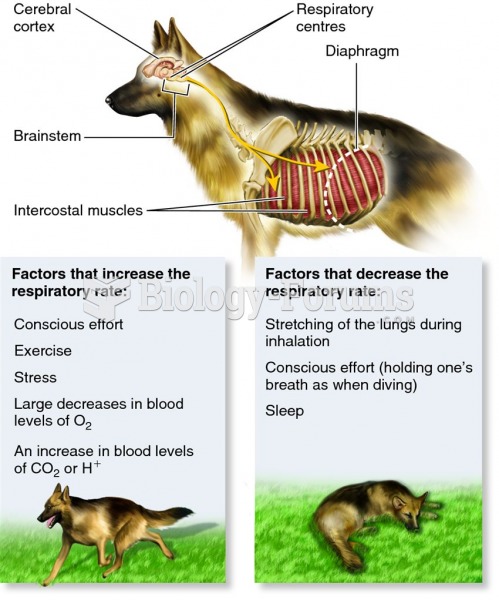
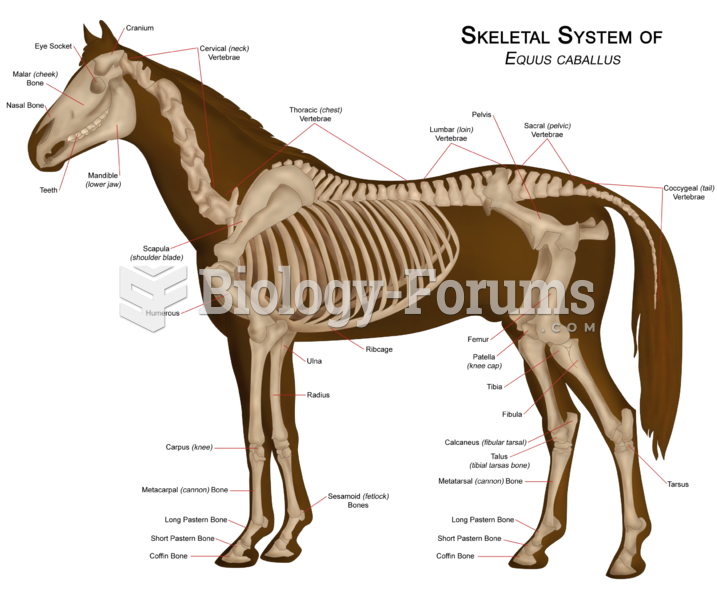
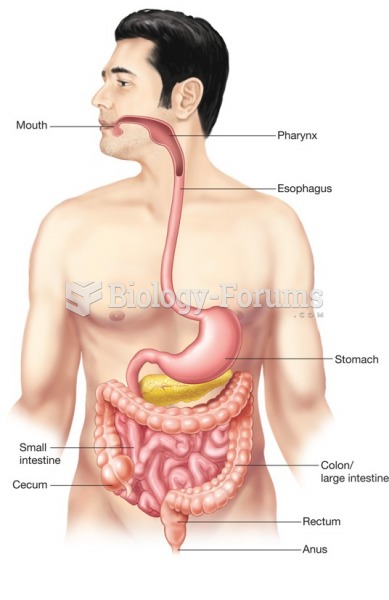
|
|
|
One way to reduce acid reflux is to lose two or three pounds. Most people lose weight in the belly area first when they increase exercise, meaning that heartburn can be reduced quickly by this method.
Ether was used widely for surgeries but became less popular because of its flammability and its tendency to cause vomiting. In England, it was quickly replaced by chloroform, but this agent caused many deaths and lost popularity.
A headache when you wake up in the morning is indicative of sinusitis. Other symptoms of sinusitis can include fever, weakness, tiredness, a cough that may be more severe at night, and a runny nose or nasal congestion.
Although the Roman numeral for the number 4 has always been taught to have been "IV," according to historians, the ancient Romans probably used "IIII" most of the time. This is partially backed up by the fact that early grandfather clocks displayed IIII for the number 4 instead of IV. Early clockmakers apparently thought that the IIII balanced out the VIII (used for the number 8) on the clock face and that it just looked better.
More than 4.4billion prescriptions were dispensed within the United States in 2016.