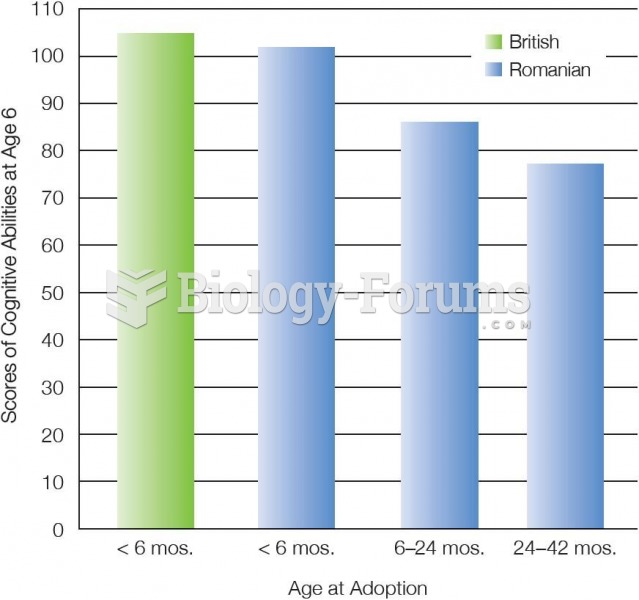
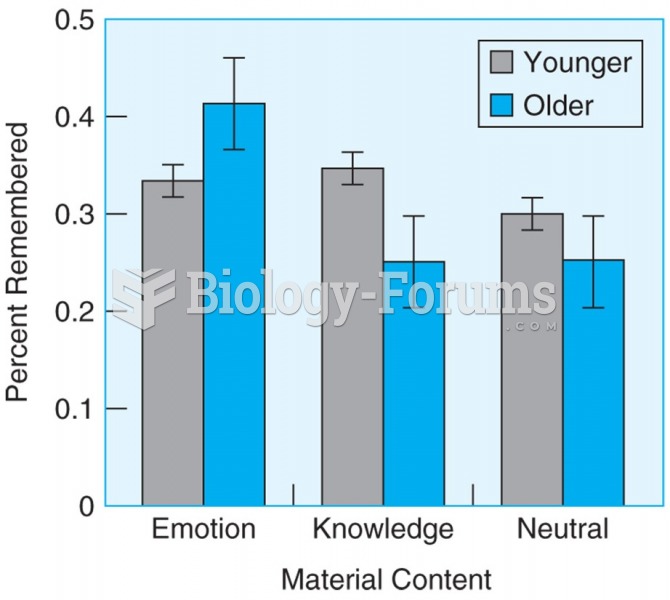
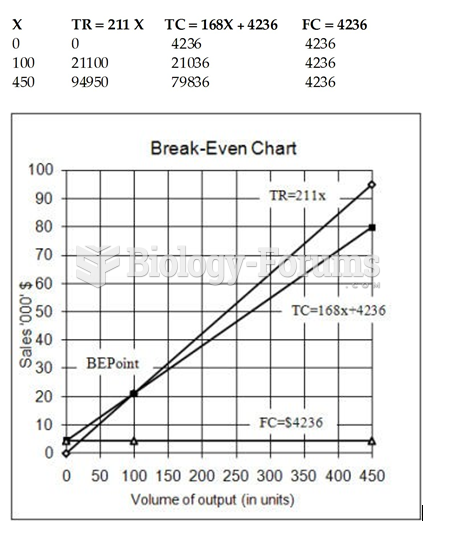
|
|
|
Between 1999 and 2012, American adults with high total cholesterol decreased from 18.3% to 12.9%
Complications of influenza include: bacterial pneumonia, ear and sinus infections, dehydration, and worsening of chronic conditions such as asthma, congestive heart failure, or diabetes.
Critical care patients are twice as likely to receive the wrong medication. Of these errors, 20% are life-threatening, and 42% require additional life-sustaining treatments.
As the western states of America were settled, pioneers often had to drink rancid water from ponds and other sources. This often resulted in chronic diarrhea, causing many cases of dehydration and death that could have been avoided if clean water had been available.
The Centers for Disease Control and Prevention has released reports detailing the deaths of infants (younger than 1 year of age) who died after being given cold and cough medications. This underscores the importance of educating parents that children younger than 2 years of age should never be given over-the-counter cold and cough medications without consulting their physicians.