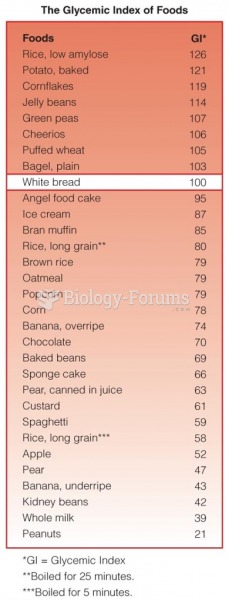
Answer to Question 1
A
Answer to Question 2
Psychological warfare PSWYAR or psychological warfare has been used by armies and terrorists across the globe to influence the enemy. PSWYAR is also synonymous with psychological operations (PSYOP) that are intended to convey selected information and indicators to foreign audiences to influence their emotions, motives, objective reasoning, and ultimately the behavior of foreign governments, organizations, groups, or individuals . Terrorist groups can use the Internet and websites to instill fear and panic by displaying images of their destruction, video footage of brutal murders, or to claim responsibility for their atrocities.
Publicity and propaganda With the advent of the Internet, terrorists no longer have to rely on traditional television, radio, or print to spread their propaganda to a regional audience. Terrorists can now operate their own websites that are available worldwide to promote their agenda, appeal to sympathizers, and even recruit others to their cause.
Data mining, research, and intelligence gathering In the same way that law enforcement should use the Internet to gather information about terrorists, they use it to gather intelligence. A wide array of information of potential interest to terrorists is available, such as location of transportation facilities, water and electrical utilities, nuclear plants, airports, shipping ports, and even counterterrorism information.
Fundraising Similar to how non-profit organizations raise funds, terrorists can use the Internet to appeal to potential donors. They can use it to set up charitable websites that serve as fronts to funnel money to terrorist organizations.
Recruitment and mobilization Terrorists can use websites and multimedia technologies to glorify their message and attract others to the cause. They can also collect information, such as the IP addresses of visitors, and attempt contact with those who seem most interested. Terrorists can also surf chat rooms or message boards and recruit from potential interested sympathizers.
Networking The Internet serves as a great vehicle to bring people together with common interests. Terrorists can use it to contact one another or network and establish contacts throughout the world. Networking can take place via email, in chat rooms, instant messaging, or on message boards.
Sharing and concealing information The Internet has made it much easier to share information about terrorism and even how to carry it out. For example, bomb making books entitled The Terrorists Handbook and The Anarchist Cookbook are widely available along with The Mujhadeen Poisons Handbook are all available online.
Planning and coordination Terrorists can use the Internet to communicate, plan, and coordinate attacks. Communications can take place in secret or password protected chat rooms and terrorists also use encryption, which can make the communications difficult to intercept and/or decipher.