This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Thyroid conditions may make getting pregnant impossible.
Did you know?
Calcitonin is a naturally occurring hormone. In women who are at least 5 years beyond menopause, it slows bone loss and increases spinal bone density.
Did you know?
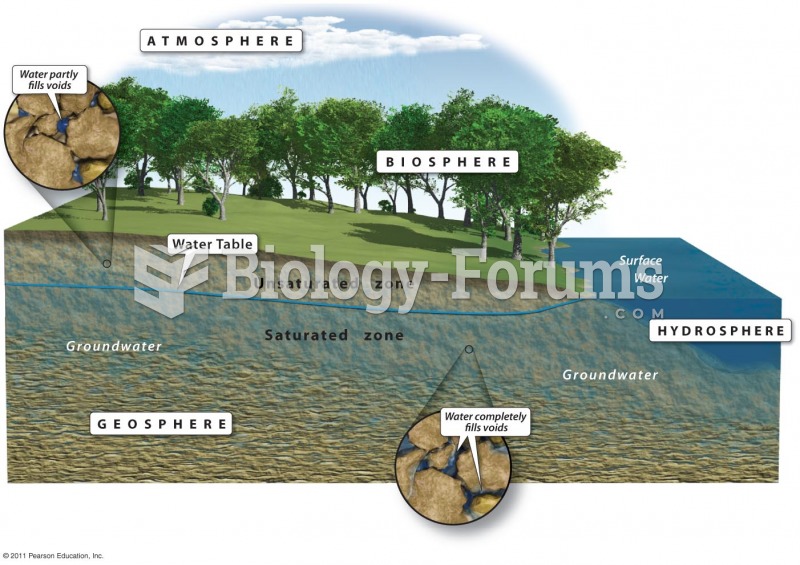
There are 60,000 miles of blood vessels in every adult human.
Did you know?
Normal urine is sterile. It contains fluids, salts, and waste products. It is free of bacteria, viruses, and fungi.
Did you know?
The Babylonians wrote numbers in a system that used 60 as the base value rather than the number 10. They did not have a symbol for "zero."