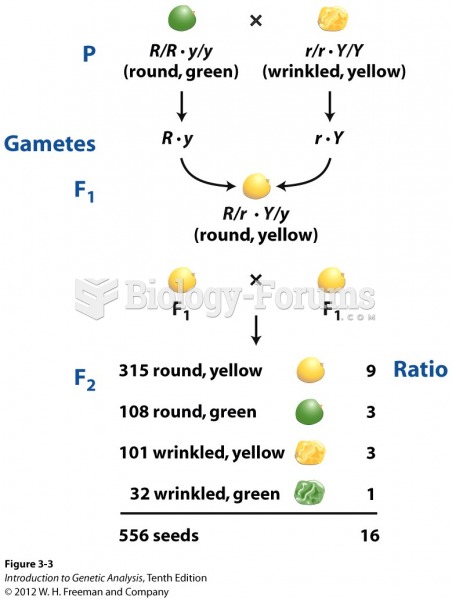
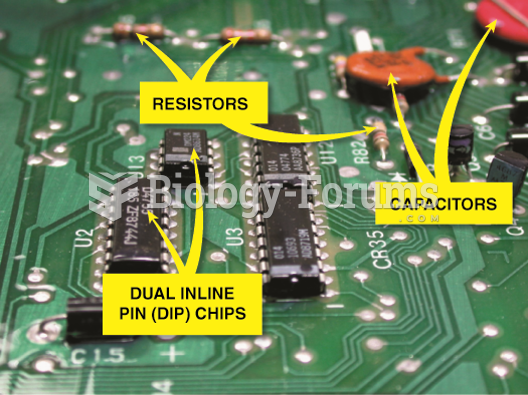
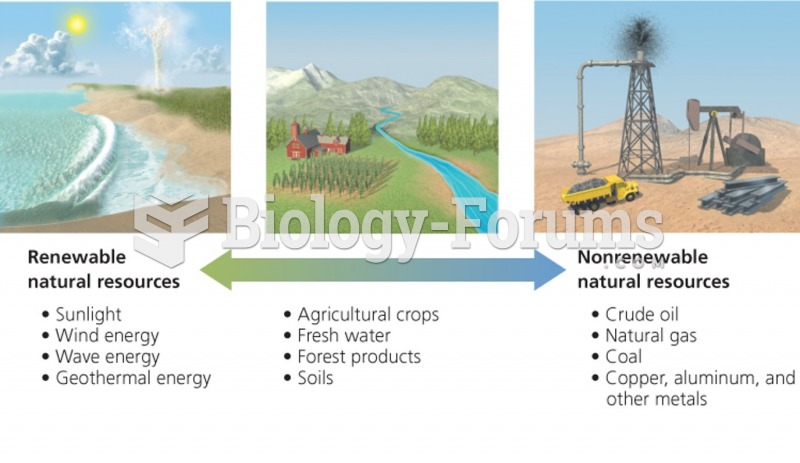
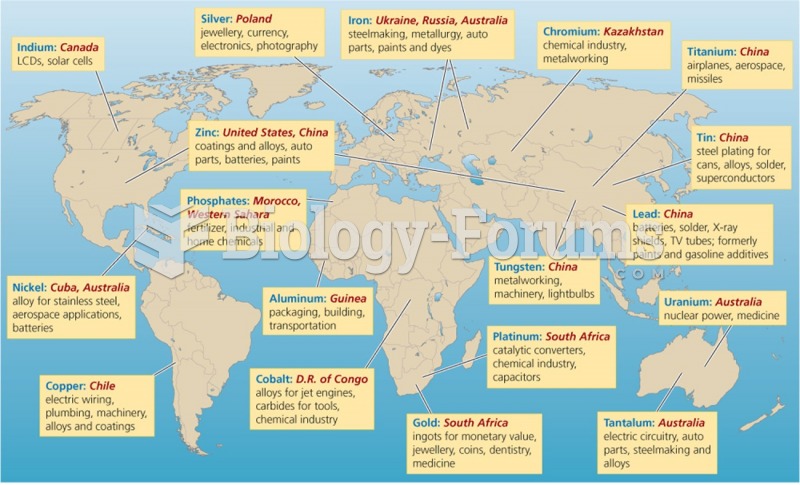
|
|
|
Stevens-Johnson syndrome and Toxic Epidermal Necrolysis syndrome are life-threatening reactions that can result in death. Complications include permanent blindness, dry-eye syndrome, lung damage, photophobia, asthma, chronic obstructive pulmonary disease, permanent loss of nail beds, scarring of mucous membranes, arthritis, and chronic fatigue syndrome. Many patients' pores scar shut, causing them to retain heat.
The U.S. Pharmacopeia Medication Errors Reporting Program states that approximately 50% of all medication errors involve insulin.
The oldest recorded age was 122. Madame Jeanne Calment was born in France in 1875 and died in 1997. She was a vegetarian and loved olive oil, port wine, and chocolate.
After 5 years of being diagnosed with rheumatoid arthritis, one every three patients will no longer be able to work.
Aspirin is the most widely used drug in the world. It has even been recognized as such by the Guinness Book of World Records.