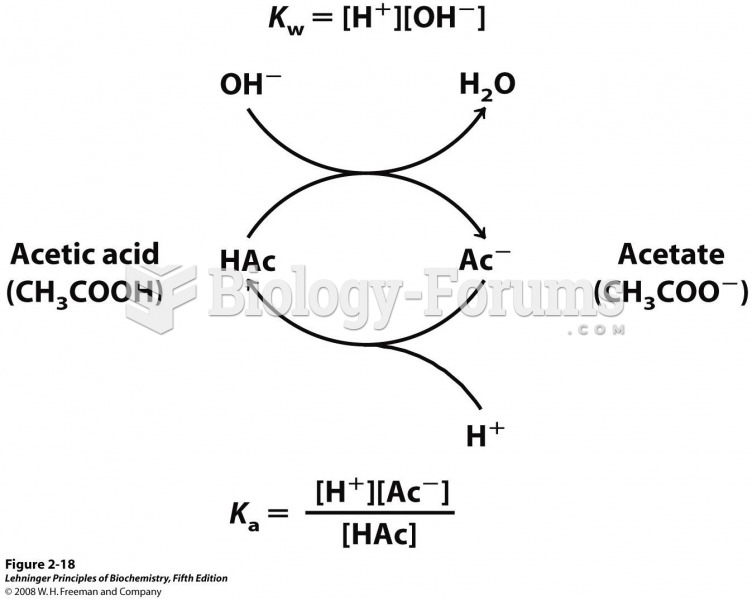
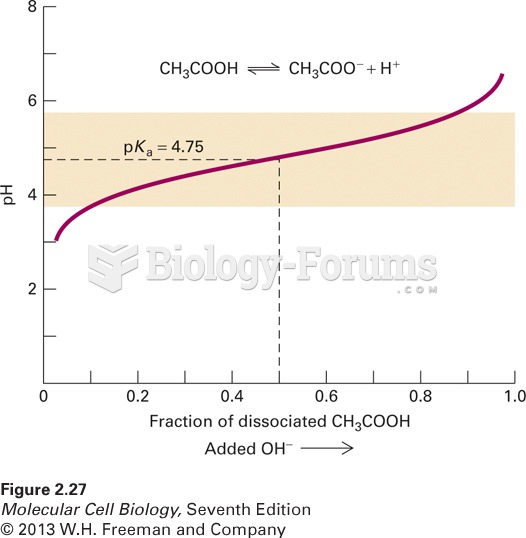
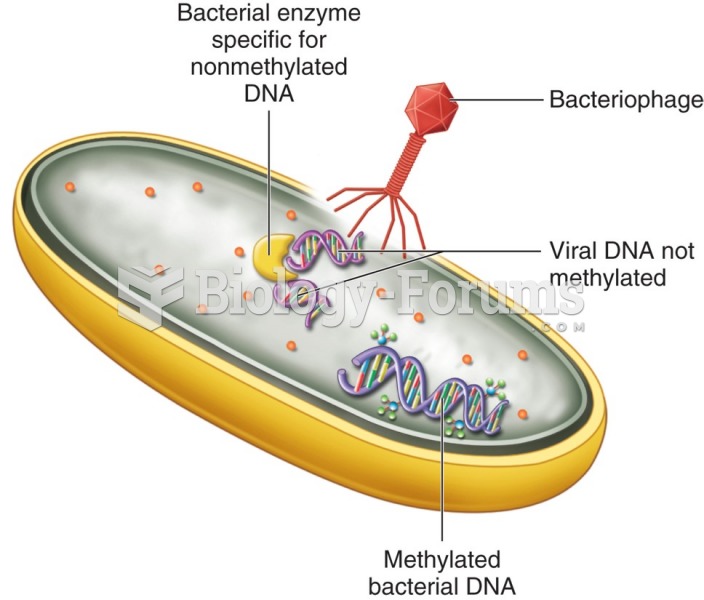
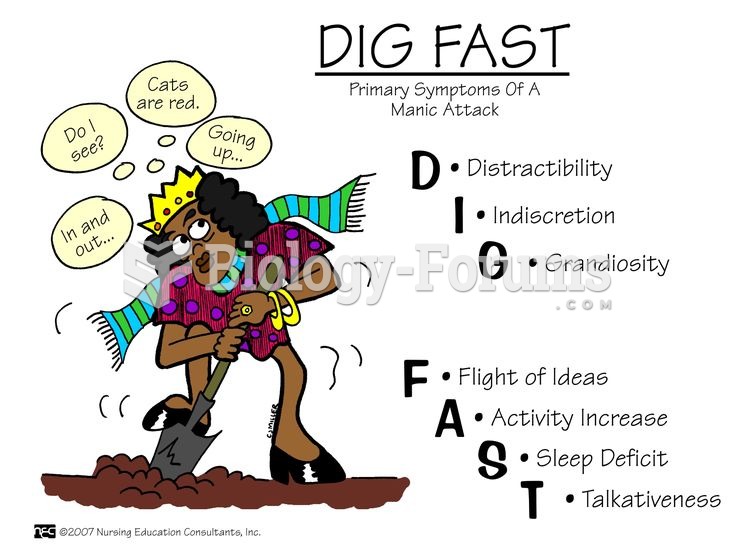
|
|
|
Aspirin is the most widely used drug in the world. It has even been recognized as such by the Guinness Book of World Records.
The first-known contraceptive was crocodile dung, used in Egypt in 2000 BC. Condoms were also reportedly used, made of animal bladders or intestines.
Eating food that has been cooked with poppy seeds may cause you to fail a drug screening test, because the seeds contain enough opiate alkaloids to register as a positive.
About 60% of newborn infants in the United States are jaundiced; that is, they look yellow. Kernicterus is a form of brain damage caused by excessive jaundice. When babies begin to be affected by excessive jaundice and begin to have brain damage, they become excessively lethargic.
Thyroid conditions cause a higher risk of fibromyalgia and chronic fatigue syndrome.