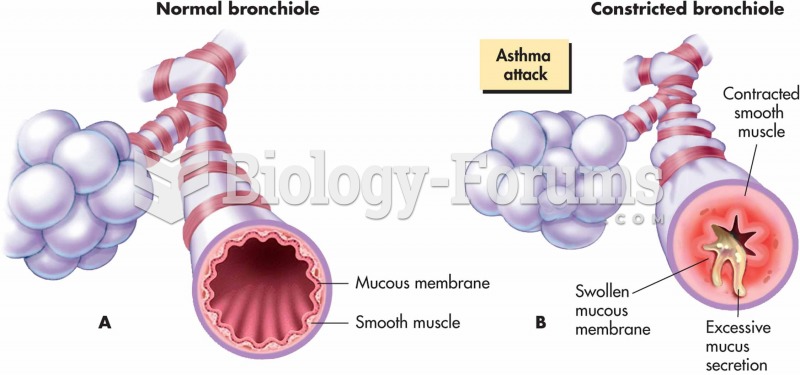
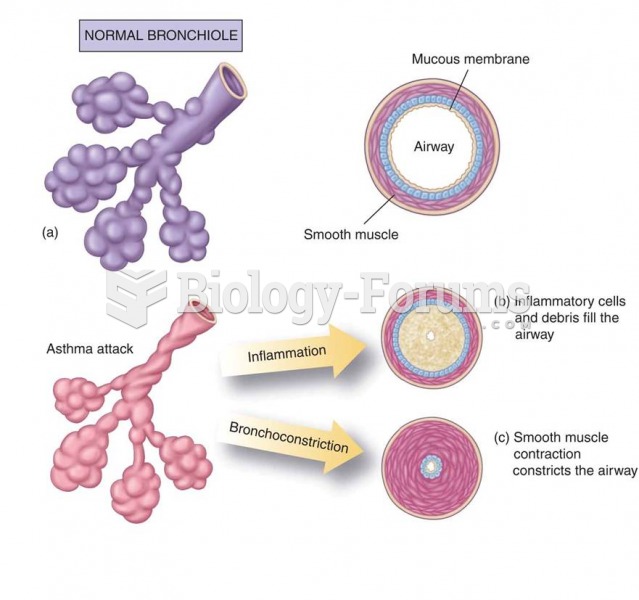
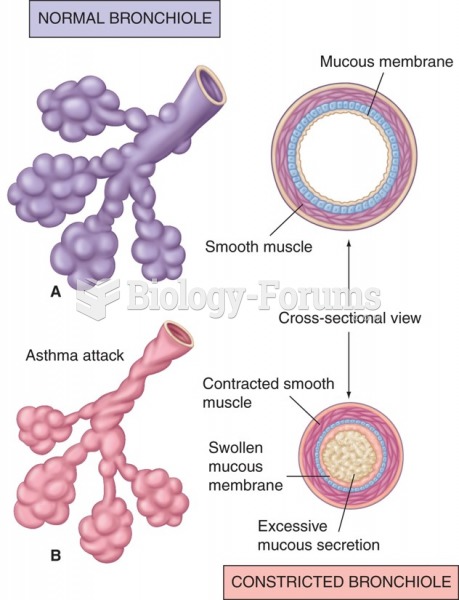
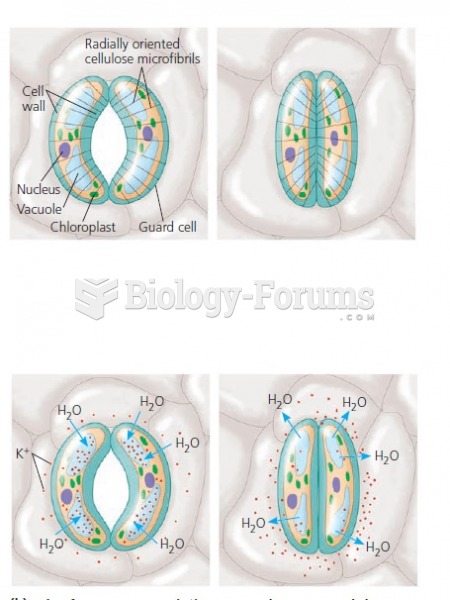
|
|
|
Many supplement containers do not even contain what their labels say. There are many documented reports of products containing much less, or more, that what is listed on their labels. They may also contain undisclosed prescription drugs and even contaminants.
In 2010, opiate painkllers, such as morphine, OxyContin®, and Vicodin®, were tied to almost 60% of drug overdose deaths.
The eye muscles are the most active muscles in the whole body. The external muscles that move the eyes are the strongest muscles in the human body for the job they have to do. They are 100 times more powerful than they need to be.
Chronic necrotizing aspergillosis has a slowly progressive process that, unlike invasive aspergillosis, does not spread to other organ systems or the blood vessels. It most often affects middle-aged and elderly individuals, spreading to surrounding tissue in the lungs. The disease often does not respond to conventionally successful treatments, and requires individualized therapies in order to keep it from becoming life-threatening.
Alcohol acts as a diuretic. Eight ounces of water is needed to metabolize just 1 ounce of alcohol.