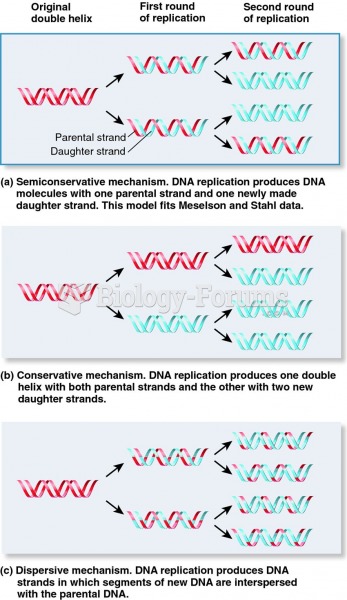
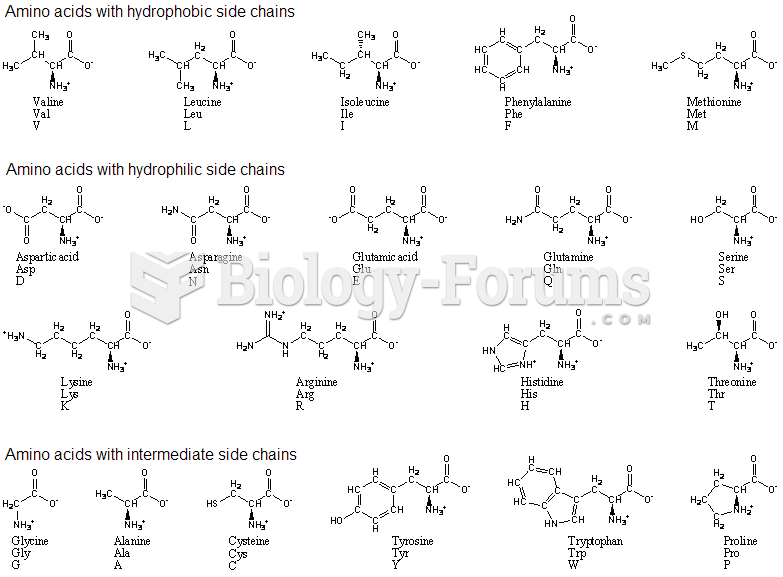
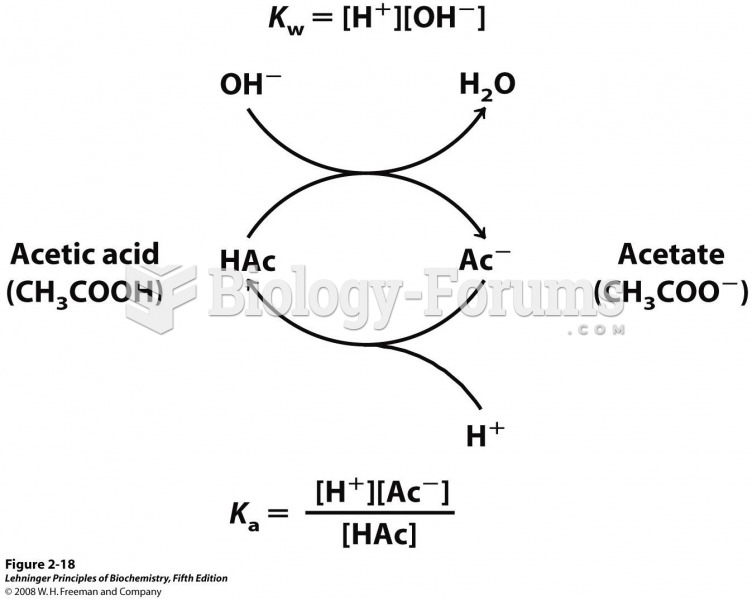
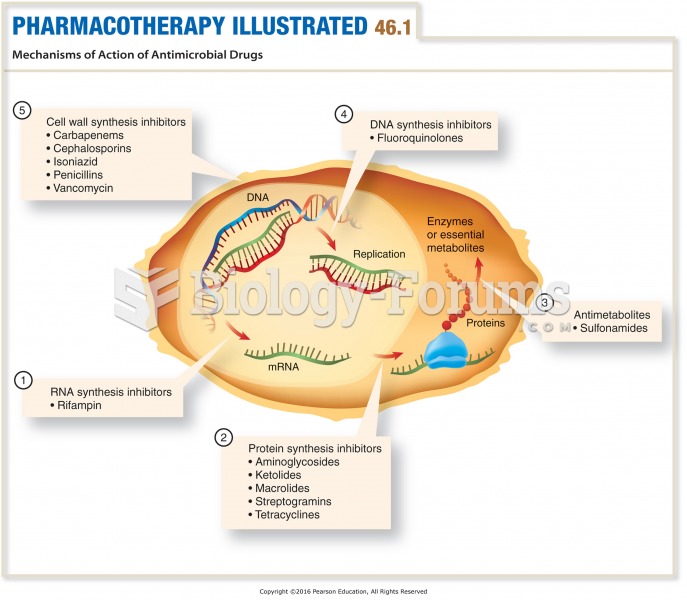
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
In 1885, the Lloyd Manufacturing Company of Albany, New York, promoted and sold "Cocaine Toothache Drops" at 15 cents per bottle! In 1914, the Harrison Narcotic Act brought the sale and distribution of this drug under federal control.
Did you know?
A headache when you wake up in the morning is indicative of sinusitis. Other symptoms of sinusitis can include fever, weakness, tiredness, a cough that may be more severe at night, and a runny nose or nasal congestion.
Did you know?
Green tea is able to stop the scent of garlic or onion from causing bad breath.
Did you know?
The B-complex vitamins and vitamin C are not stored in the body and must be replaced each day.
Did you know?
The first documented use of surgical anesthesia in the United States was in Connecticut in 1844.