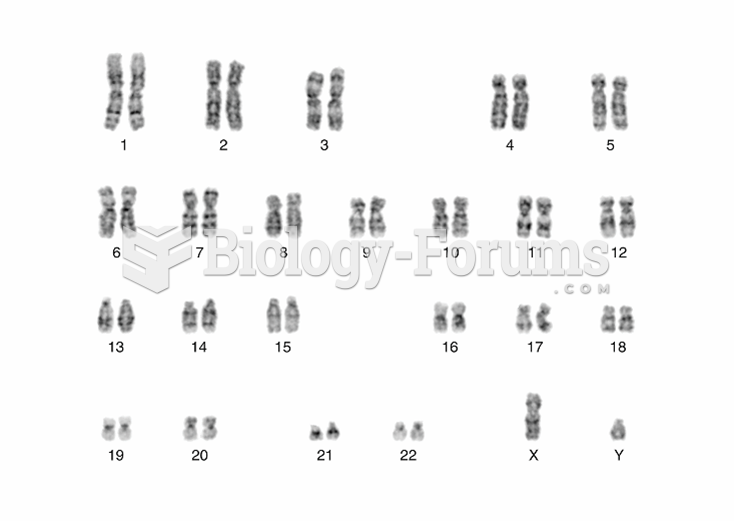
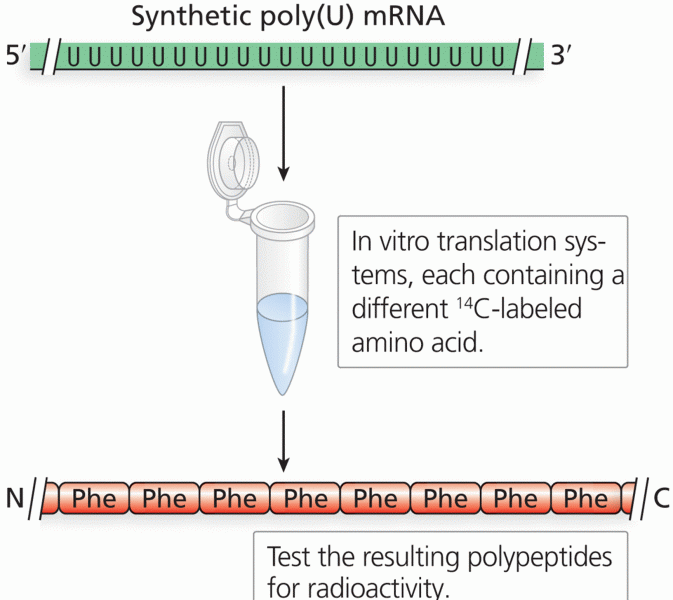
|
|
|
When blood is deoxygenated and flowing back to the heart through the veins, it is dark reddish-blue in color. Blood in the arteries that is oxygenated and flowing out to the body is bright red. Whereas arterial blood comes out in spurts, venous blood flows.
The Food and Drug Administration has approved Risperdal, an adult antipsychotic drug, for the symptomatic treatment of irritability in children and adolescents with autism. The approval is the first for the use of a drug to treat behaviors associated with autism in children. These behaviors are included under the general heading of irritability and include aggression, deliberate self-injury, and temper tantrums.
Inotropic therapy does not have a role in the treatment of most heart failure patients. These drugs can make patients feel and function better but usually do not lengthen the predicted length of their lives.
More than 2,500 barbiturates have been synthesized. At the height of their popularity, about 50 were marketed for human use.
There are 60,000 miles of blood vessels in every adult human.