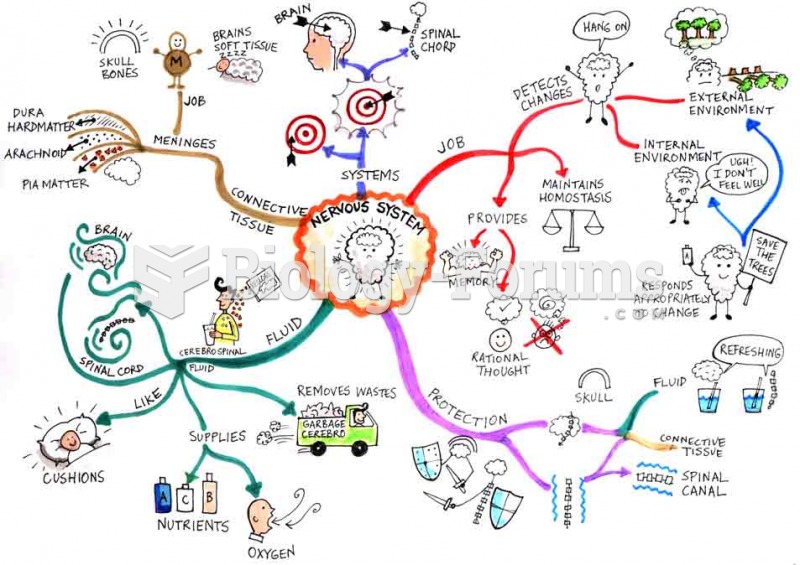
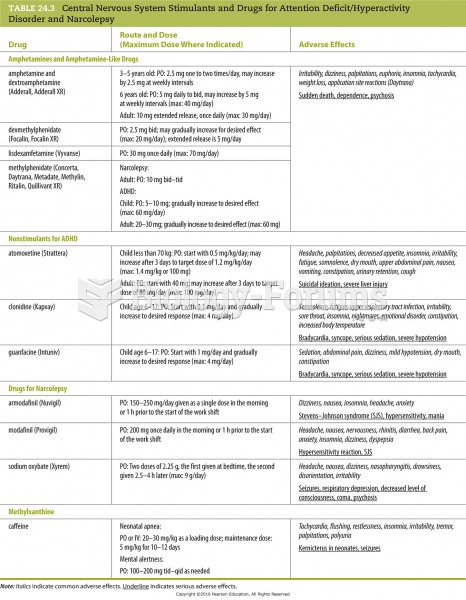
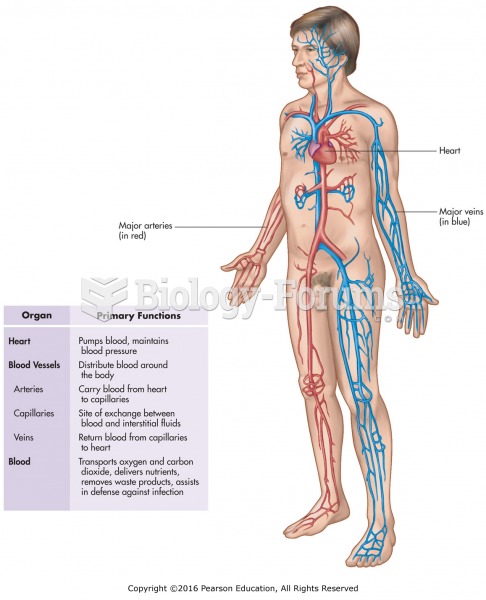
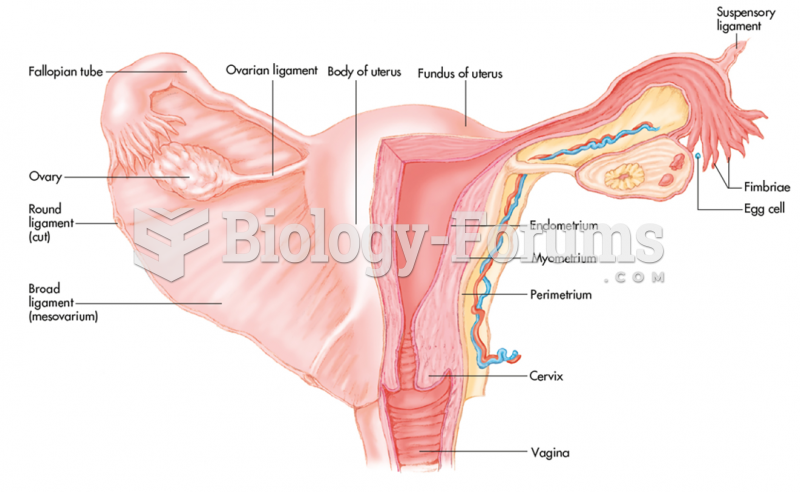
|
|
|
Liver spots have nothing whatsoever to do with the liver. They are a type of freckles commonly seen in older adults who have been out in the sun without sufficient sunscreen.
Oliver Wendell Holmes is credited with introducing the words "anesthesia" and "anesthetic" into the English language in 1846.
Cocaine was isolated in 1860 and first used as a local anesthetic in 1884. Its first clinical use was by Sigmund Freud to wean a patient from morphine addiction. The fictional character Sherlock Holmes was supposed to be addicted to cocaine by injection.
Chronic necrotizing aspergillosis has a slowly progressive process that, unlike invasive aspergillosis, does not spread to other organ systems or the blood vessels. It most often affects middle-aged and elderly individuals, spreading to surrounding tissue in the lungs. The disease often does not respond to conventionally successful treatments, and requires individualized therapies in order to keep it from becoming life-threatening.
For about 100 years, scientists thought that peptic ulcers were caused by stress, spicy food, and alcohol. Later, researchers added stomach acid to the list of causes and began treating ulcers with antacids. Now it is known that peptic ulcers are predominantly caused by Helicobacter pylori, a spiral-shaped bacterium that normally exist in the stomach.