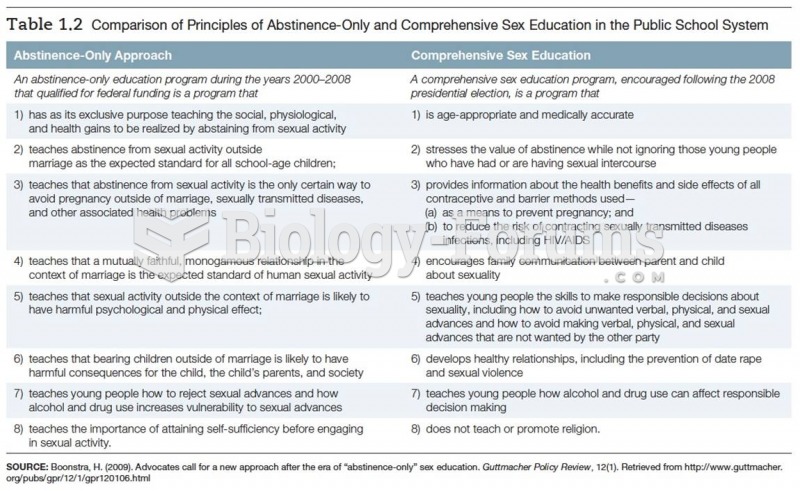
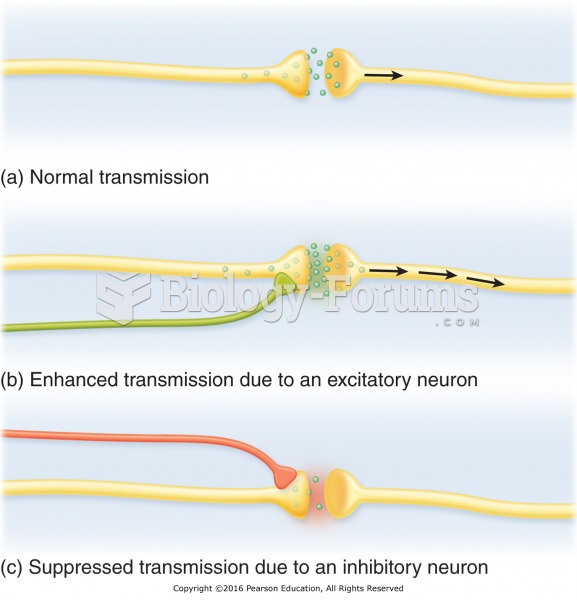
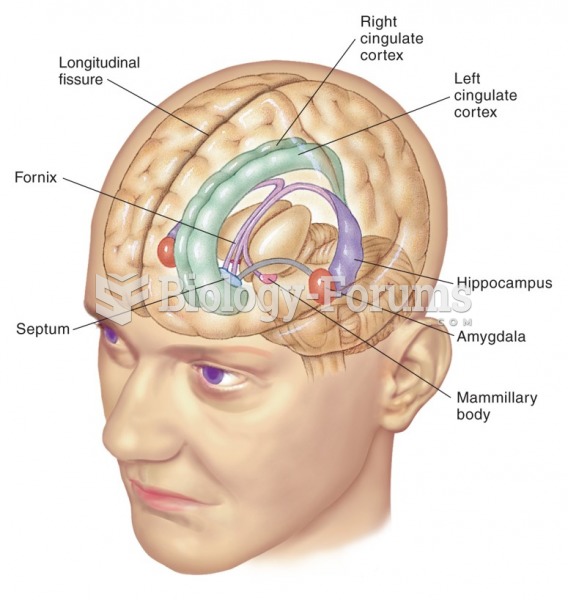
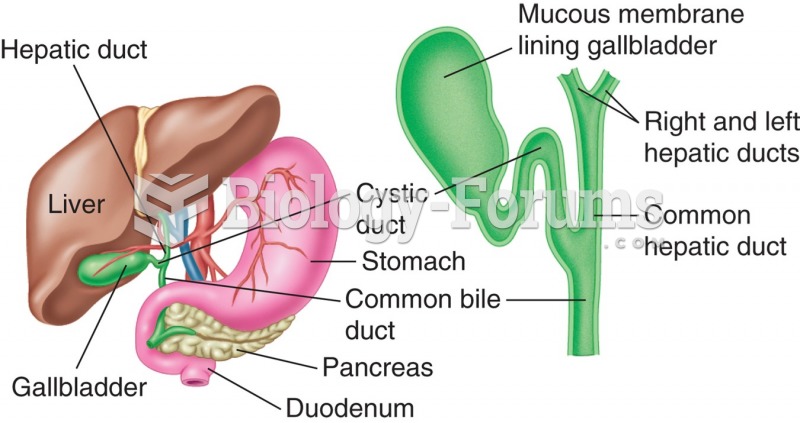
|
|
|
IgA antibodies protect body surfaces exposed to outside foreign substances. IgG antibodies are found in all body fluids. IgM antibodies are the first type of antibody made in response to an infection. IgE antibody levels are often high in people with allergies. IgD antibodies are found in tissues lining the abdomen and chest.
According to the CDC, approximately 31.7% of the U.S. population has high low-density lipoprotein (LDL) or "bad cholesterol" levels.
Anti-aging claims should not ever be believed. There is no supplement, medication, or any other substance that has been proven to slow or stop the aging process.
To prove that stomach ulcers were caused by bacteria and not by stress, a researcher consumed an entire laboratory beaker full of bacterial culture. After this, he did indeed develop stomach ulcers, and won the Nobel Prize for his discovery.
To maintain good kidney function, you should drink at least 3 quarts of water daily. Water dilutes urine and helps prevent concentrations of salts and minerals that can lead to kidney stone formation. Chronic dehydration is a major contributor to the development of kidney stones.