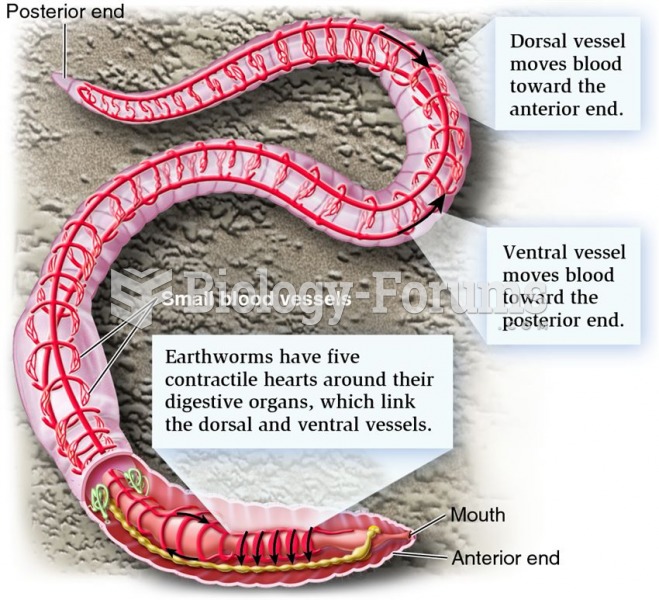
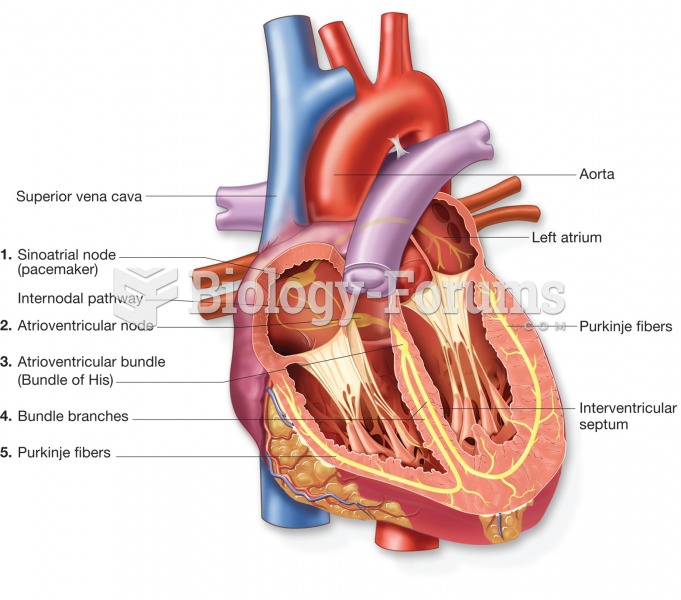
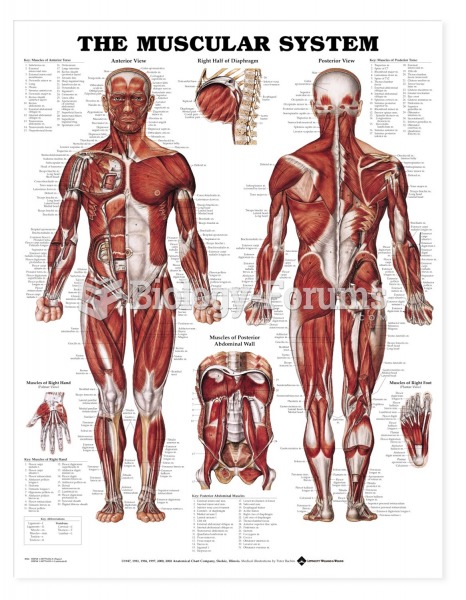
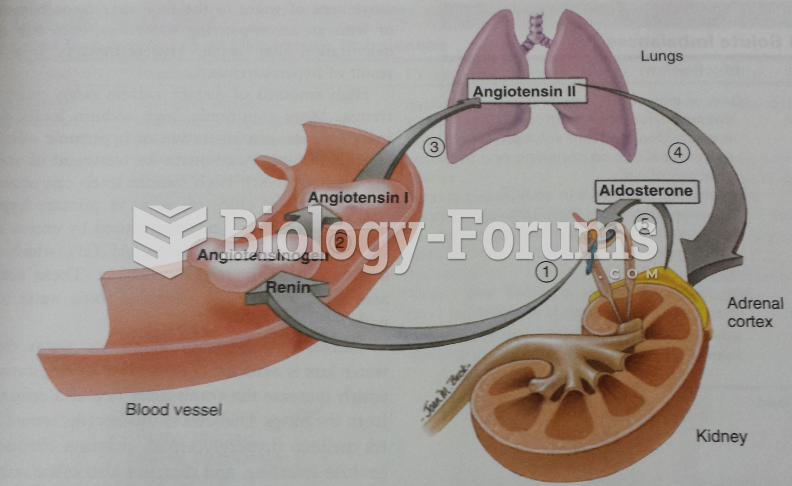
|
|
|
Approximately 70% of expectant mothers report experiencing some symptoms of morning sickness during the first trimester of pregnancy.
More than 20 million Americans cite use of marijuana within the past 30 days, according to the National Survey on Drug Use and Health (NSDUH). More than 8 million admit to using it almost every day.
Allergies play a major part in the health of children. The most prevalent childhood allergies are milk, egg, soy, wheat, peanuts, tree nuts, and seafood.
Children of people with alcoholism are more inclined to drink alcohol or use hard drugs. In fact, they are 400 times more likely to use hard drugs than those who do not have a family history of alcohol addiction.
In the United States, there is a birth every 8 seconds, according to the U.S. Census Bureau's Population Clock.