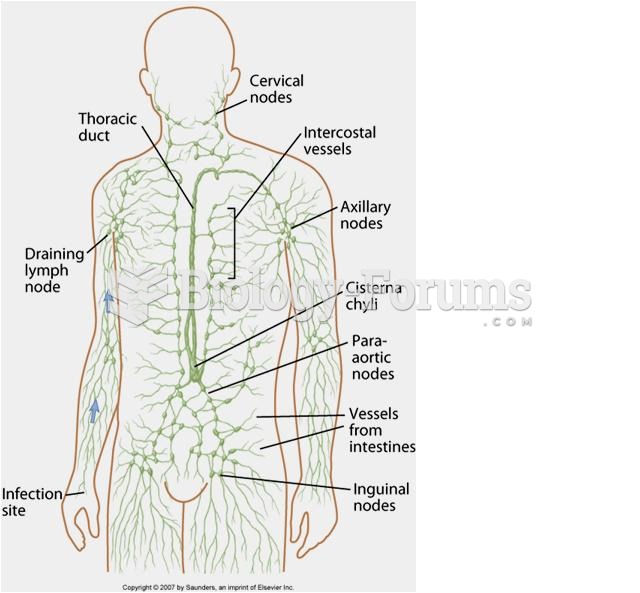
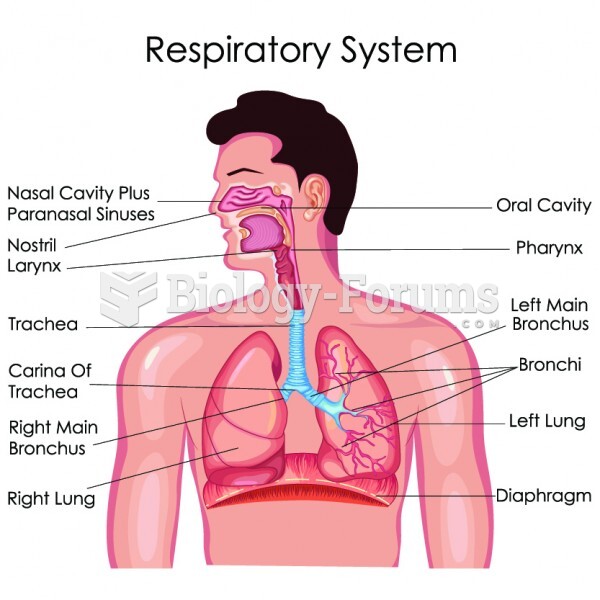
|
|
|
Amphetamine poisoning can cause intravascular coagulation, circulatory collapse, rhabdomyolysis, ischemic colitis, acute psychosis, hyperthermia, respiratory distress syndrome, and pericarditis.
More than 150,000 Americans killed by cardiovascular disease are younger than the age of 65 years.
Stevens-Johnson syndrome and Toxic Epidermal Necrolysis syndrome are life-threatening reactions that can result in death. Complications include permanent blindness, dry-eye syndrome, lung damage, photophobia, asthma, chronic obstructive pulmonary disease, permanent loss of nail beds, scarring of mucous membranes, arthritis, and chronic fatigue syndrome. Many patients' pores scar shut, causing them to retain heat.
There are more nerve cells in one human brain than there are stars in the Milky Way.
Computer programs are available that crosscheck a new drug's possible trade name with all other trade names currently available. These programs detect dangerous similarities between names and alert the manufacturer of the drug.