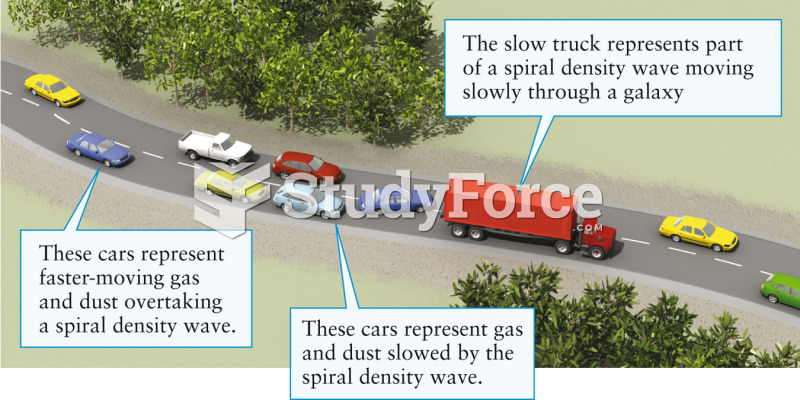
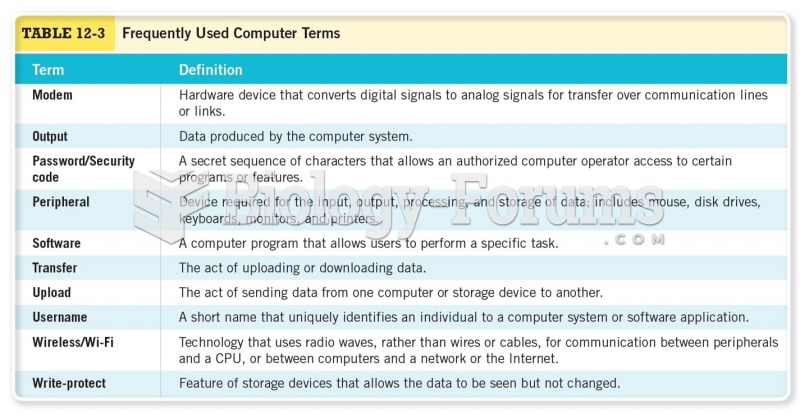
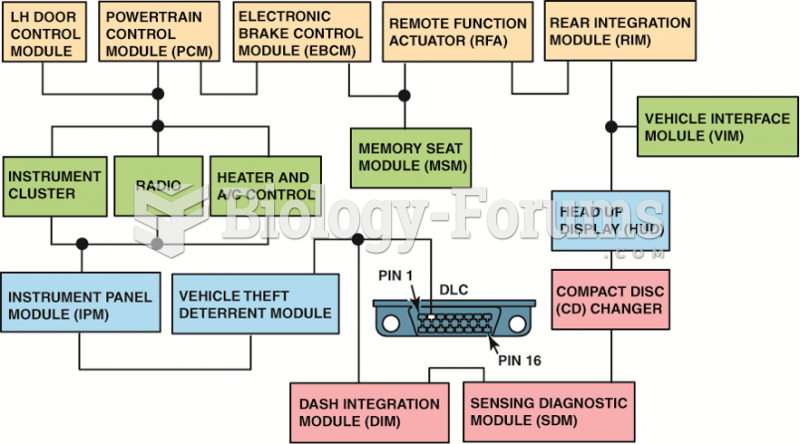
|
|
|
An identified risk factor for osteoporosis is the intake of excessive amounts of vitamin A. Dietary intake of approximately double the recommended daily amount of vitamin A, by women, has been shown to reduce bone mineral density and increase the chances for hip fractures compared with women who consumed the recommended daily amount (or less) of vitamin A.
More than 20 million Americans cite use of marijuana within the past 30 days, according to the National Survey on Drug Use and Health (NSDUH). More than 8 million admit to using it almost every day.
Cytomegalovirus affects nearly the same amount of newborns every year as Down syndrome.
Parkinson's disease is both chronic and progressive. This means that it persists over a long period of time and that its symptoms grow worse over time.
A seasonal flu vaccine is the best way to reduce the chances you will get seasonal influenza and spread it to others.