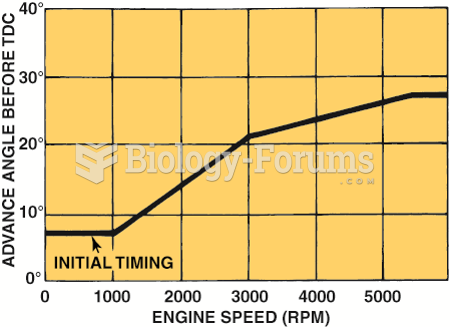
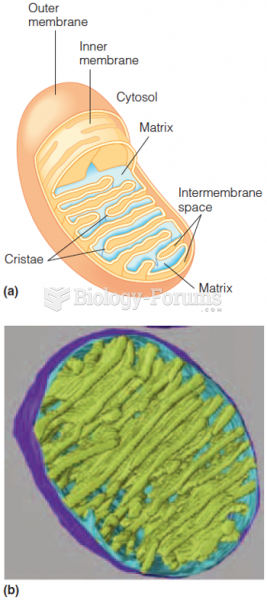
|
|
|
The word drug comes from the Dutch word droog (meaning "dry"). For centuries, most drugs came from dried plants, hence the name.
According to the National Institute of Environmental Health Sciences, lung disease is the third leading killer in the United States, responsible for one in seven deaths. It is the leading cause of death among infants under the age of one year.
Medications that are definitely not safe to take when breastfeeding include radioactive drugs, antimetabolites, some cancer (chemotherapy) agents, bromocriptine, ergotamine, methotrexate, and cyclosporine.
Signs and symptoms of a drug overdose include losing consciousness, fever or sweating, breathing problems, abnormal pulse, and changes in skin color.
Vital signs (blood pressure, temperature, pulse rate, respiration rate) should be taken before any drug administration. Patients should be informed not to use tobacco or caffeine at least 30 minutes before their appointment.