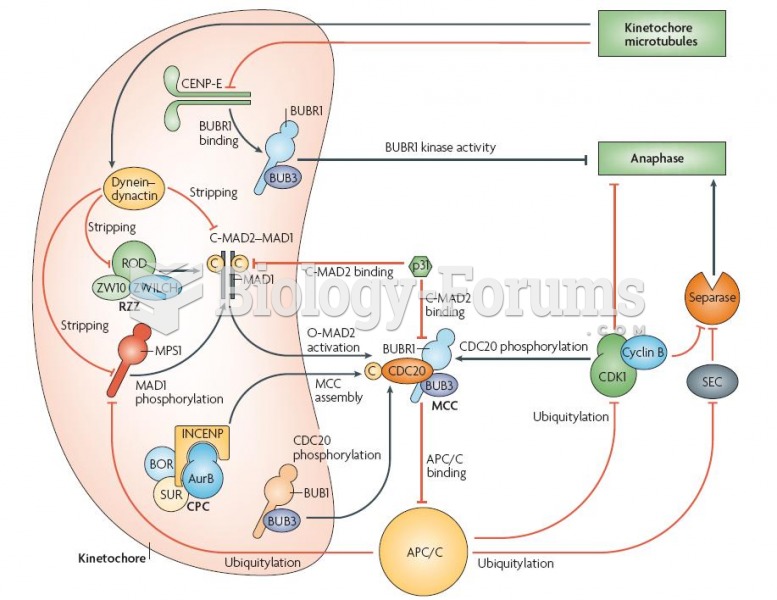
|
|
|
Human stomach acid is strong enough to dissolve small pieces of metal such as razor blades or staples.
Throughout history, plants containing cardiac steroids have been used as heart drugs and as poisons (e.g., in arrows used in combat), emetics, and diuretics.
There are more nerve cells in one human brain than there are stars in the Milky Way.
As the western states of America were settled, pioneers often had to drink rancid water from ponds and other sources. This often resulted in chronic diarrhea, causing many cases of dehydration and death that could have been avoided if clean water had been available.
Never take aspirin without food because it is likely to irritate your stomach. Never give aspirin to children under age 12. Overdoses of aspirin have the potential to cause deafness.
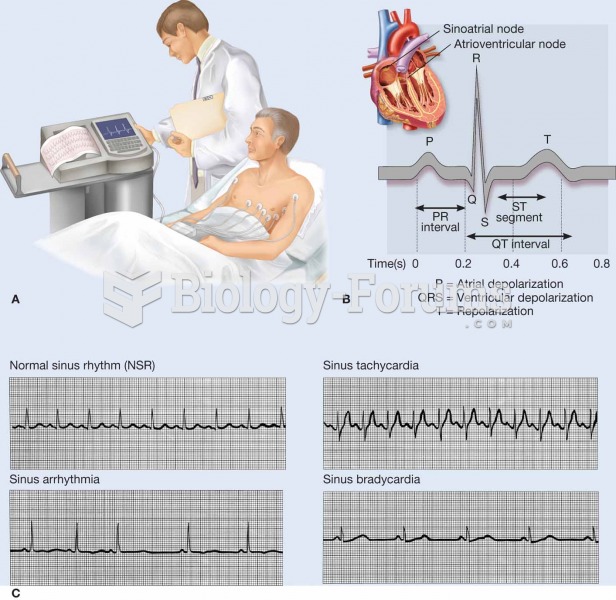 An electrocardiogram (ECG, EKG) is a commonly used procedure in which the electrical events associat
An electrocardiogram (ECG, EKG) is a commonly used procedure in which the electrical events associat
 James A. Garfield lies mortally wounded. After failing to locate the bullet, surgeons called in Alex
James A. Garfield lies mortally wounded. After failing to locate the bullet, surgeons called in Alex