|
|
|
People with alcoholism are at a much greater risk of malnutrition than are other people and usually exhibit low levels of most vitamins (especially folic acid). This is because alcohol often takes the place of 50% of their daily intake of calories, with little nutritional value contained in it.
A strange skin disease referred to as Morgellons has occurred in the southern United States and in California. Symptoms include slowly healing sores, joint pain, persistent fatigue, and a sensation of things crawling through the skin. Another symptom is strange-looking, threadlike extrusions coming out of the skin.
There are approximately 3 million unintended pregnancies in the United States each year.
A serious new warning has been established for pregnant women against taking ACE inhibitors during pregnancy. In the study, the risk of major birth defects in children whose mothers took ACE inhibitors during the first trimester was nearly three times higher than in children whose mothers didn't take ACE inhibitors. Physicians can prescribe alternative medications for pregnant women who have symptoms of high blood pressure.
Eat fiber! A diet high in fiber can help lower cholesterol levels by as much as 10%.
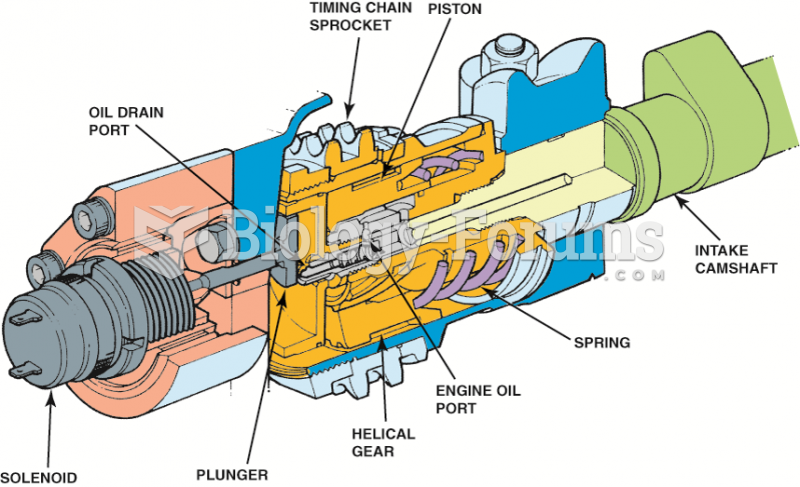 A typical variable cam timing control valve. The solenoid is controlled by the engine computer and ...
A typical variable cam timing control valve. The solenoid is controlled by the engine computer and ...
 Checking the 5 volt reference from the computer being applied to the TP sensor with the ignition ...
Checking the 5 volt reference from the computer being applied to the TP sensor with the ignition ...