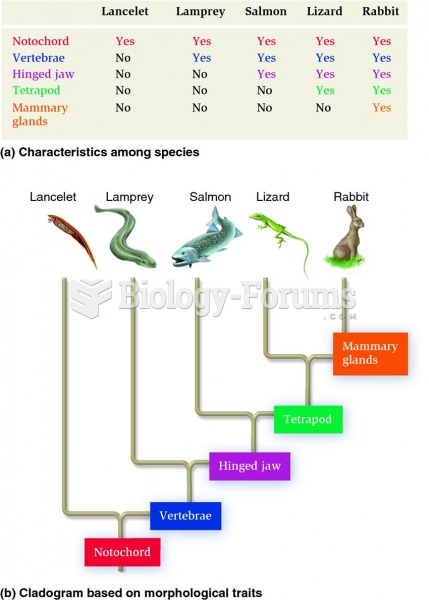
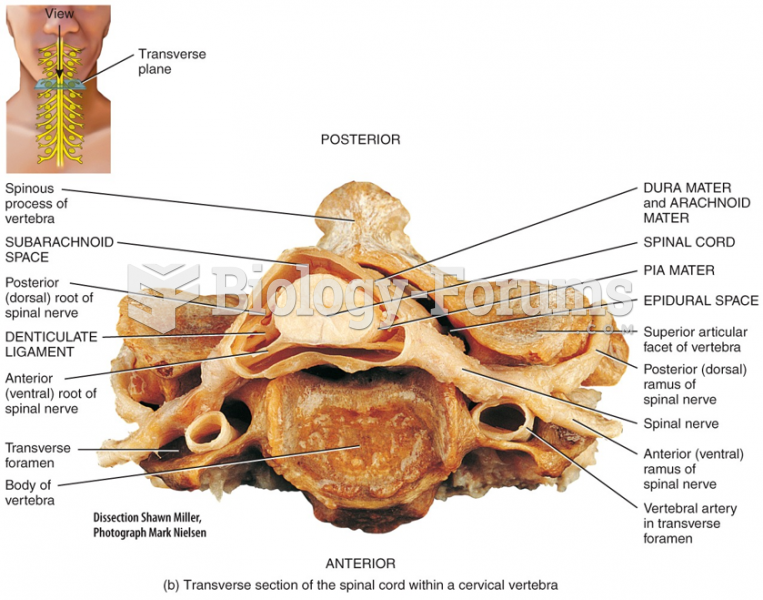
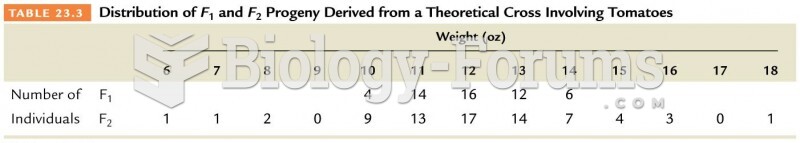
|
|
|
Astigmatism is the most common vision problem. It may accompany nearsightedness or farsightedness. It is usually caused by an irregularly shaped cornea, but sometimes it is the result of an irregularly shaped lens. Either type can be corrected by eyeglasses, contact lenses, or refractive surgery.
The term bacteria was devised in the 19th century by German biologist Ferdinand Cohn. He based it on the Greek word "bakterion" meaning a small rod or staff. Cohn is considered to be the father of modern bacteriology.
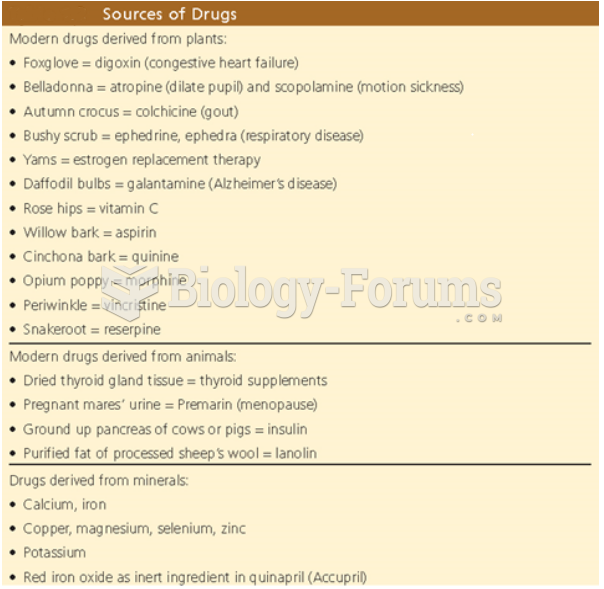
Aspirin is the most widely used drug in the world. It has even been recognized as such by the Guinness Book of World Records.
There are more sensory neurons in the tongue than in any other part of the body.
Hip fractures are the most serious consequences of osteoporosis. The incidence of hip fractures increases with each decade among patients in their 60s to patients in their 90s for both women and men of all populations. Men and women older than 80 years of age show the highest incidence of hip fractures.