|
|
|
People with alcoholism are at a much greater risk of malnutrition than are other people and usually exhibit low levels of most vitamins (especially folic acid). This is because alcohol often takes the place of 50% of their daily intake of calories, with little nutritional value contained in it.
A cataract is a clouding of the eyes' natural lens. As we age, some clouding of the lens may occur. The first sign of a cataract is usually blurry vision. Although glasses and other visual aids may at first help a person with cataracts, surgery may become inevitable. Cataract surgery is very successful in restoring vision, and it is the most frequently performed surgery in the United States.
The liver is the only organ that has the ability to regenerate itself after certain types of damage. As much as 25% of the liver can be removed, and it will still regenerate back to its original shape and size. However, the liver cannot regenerate after severe damage caused by alcohol.
Alcohol acts as a diuretic. Eight ounces of water is needed to metabolize just 1 ounce of alcohol.
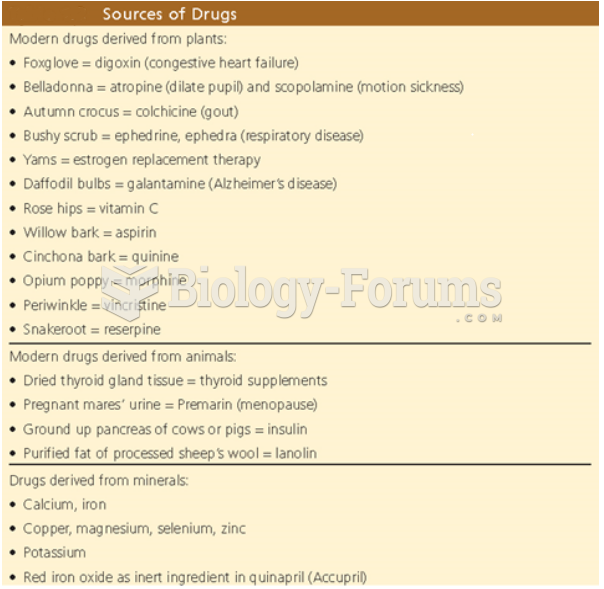
Warfarin was developed as a consequence of the study of a strange bleeding disorder that suddenly occurred in cattle on the northern prairies of the United States in the early 1900s.