|
|
|
Did you know?
About 3% of all pregnant women will give birth to twins, which is an increase in rate of nearly 60% since the early 1980s.
Did you know?
Today, nearly 8 out of 10 pregnant women living with HIV (about 1.1 million), receive antiretrovirals.
Did you know?
About 600,000 particles of skin are shed every hour by each human. If you live to age 70 years, you have shed 105 pounds of dead skin.
Did you know?
The U.S. Pharmacopeia Medication Errors Reporting Program states that approximately 50% of all medication errors involve insulin.
Did you know?
Eating carrots will improve your eyesight. Carrots are high in vitamin A (retinol), which is essential for good vision. It can also be found in milk, cheese, egg yolks, and liver.
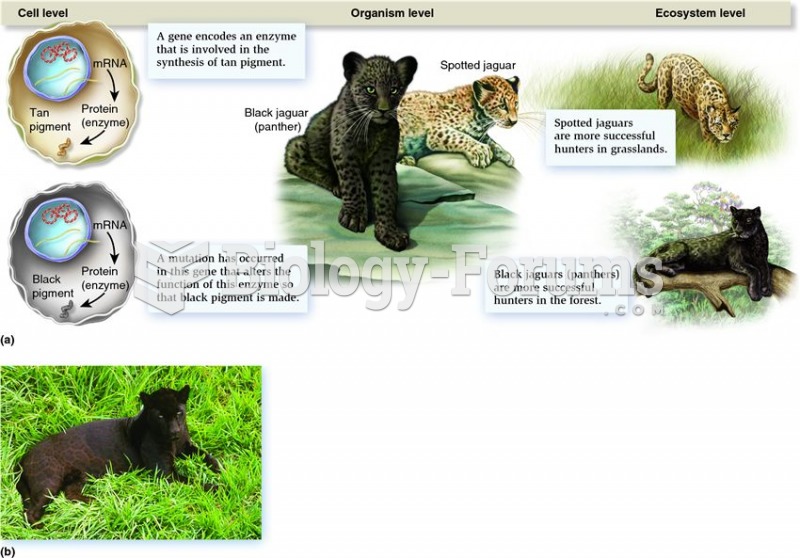 How the study of genomes and proteomes can provide us with connections to different biological level
How the study of genomes and proteomes can provide us with connections to different biological level
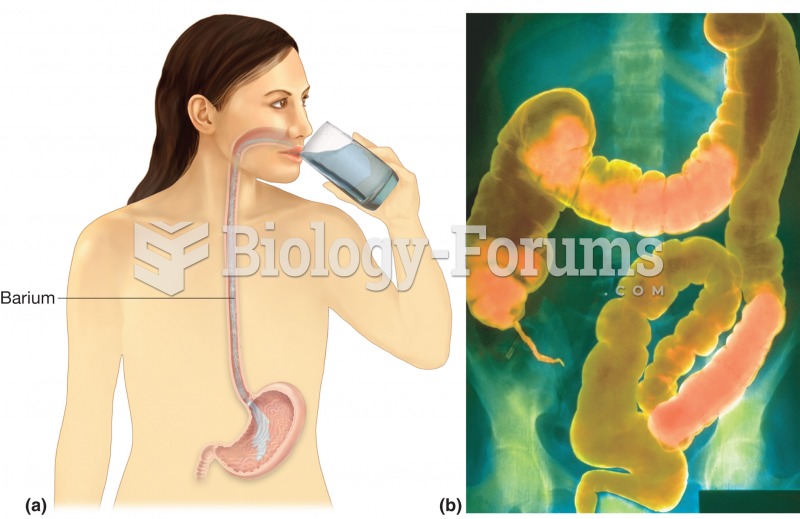 GI series. (a) Upper GI series begins with a barium swallow, barium shake, or barium meal. (b) Lower
GI series. (a) Upper GI series begins with a barium swallow, barium shake, or barium meal. (b) Lower
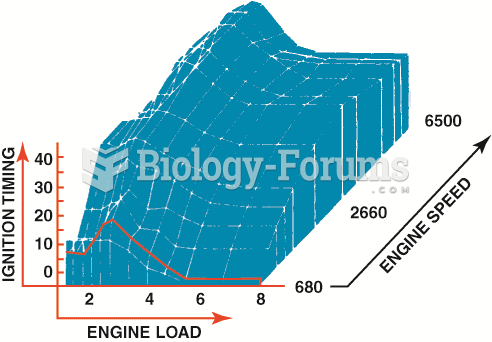
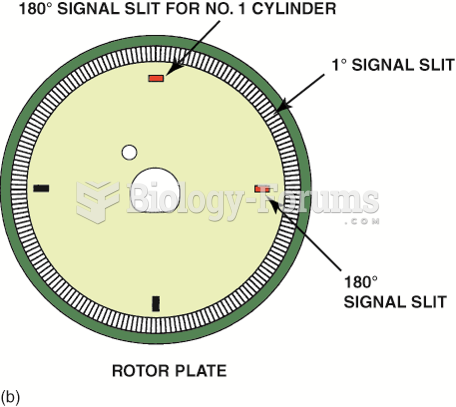 Cylinder 1 slit signals the computer the piston position for cylinder 1. The 1-degree slits provide ...
Cylinder 1 slit signals the computer the piston position for cylinder 1. The 1-degree slits provide ...