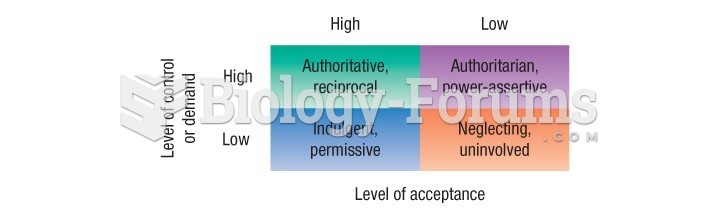
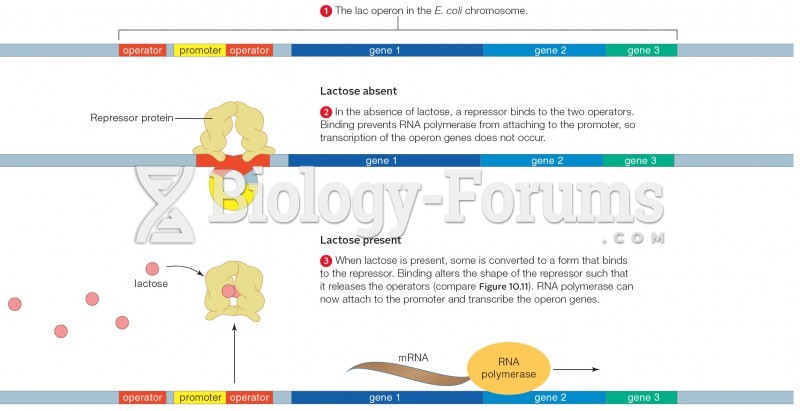
|
|
|
The first monoclonal antibodies were made exclusively from mouse cells. Some are now fully human, which means they are likely to be safer and may be more effective than older monoclonal antibodies.
To combat osteoporosis, changes in lifestyle and diet are recommended. At-risk patients should include 1,200 to 1,500 mg of calcium daily either via dietary means or with supplements.
The Centers for Disease Control and Prevention (CDC) was originally known as the Communicable Disease Center, which was formed to fight malaria. It was originally headquartered in Atlanta, Georgia, since the Southern states faced the worst threat from malaria.
The tallest man ever known was Robert Wadlow, an American, who reached the height of 8 feet 11 inches. He died at age 26 years from an infection caused by the immense weight of his body (491 pounds) and the stress on his leg bones and muscles.
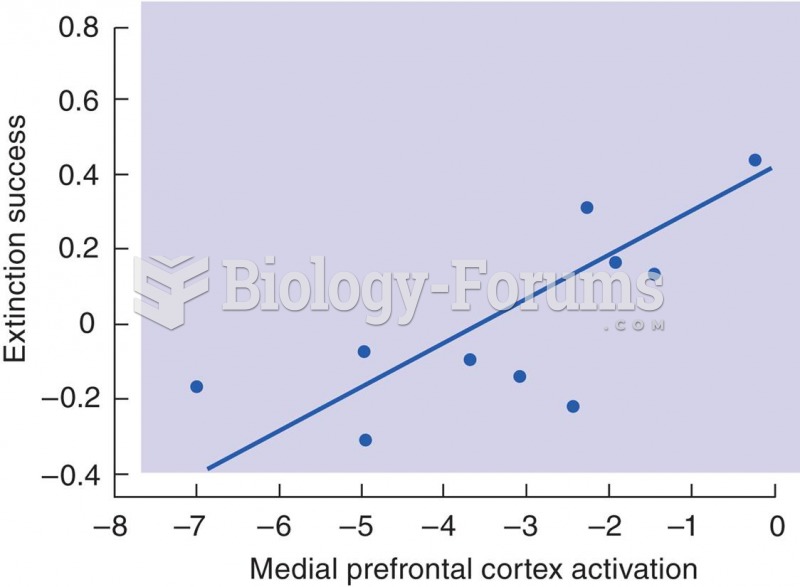
Studies show that systolic blood pressure can be significantly lowered by taking statins. In fact, the higher the patient's baseline blood pressure, the greater the effect of statins on his or her blood pressure.