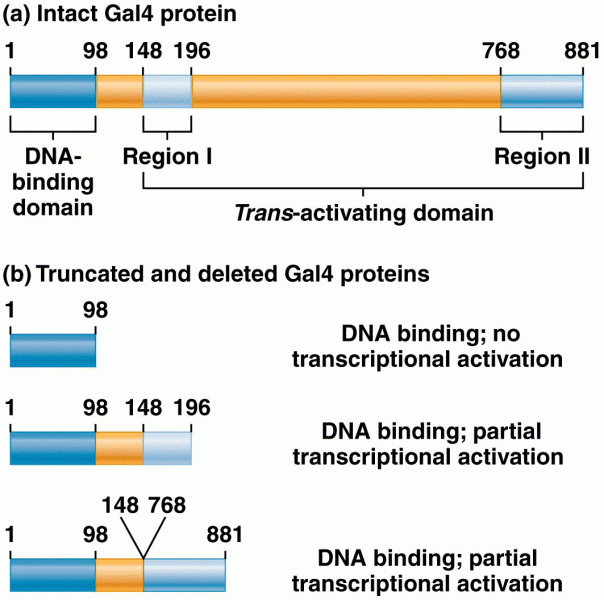
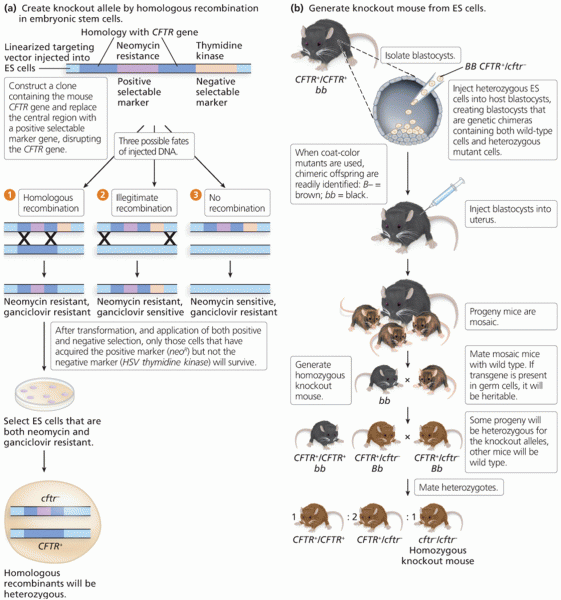
|
|
|
Astigmatism is the most common vision problem. It may accompany nearsightedness or farsightedness. It is usually caused by an irregularly shaped cornea, but sometimes it is the result of an irregularly shaped lens. Either type can be corrected by eyeglasses, contact lenses, or refractive surgery.
Each year in the United States, there are approximately six million pregnancies. This means that at any one time, about 4% of women in the United States are pregnant.
In 2010, opiate painkllers, such as morphine, OxyContin®, and Vicodin®, were tied to almost 60% of drug overdose deaths.
The cure for trichomoniasis is easy as long as the patient does not drink alcoholic beverages for 24 hours. Just a single dose of medication is needed to rid the body of the disease. However, without proper precautions, an individual may contract the disease repeatedly. In fact, most people develop trichomoniasis again within three months of their last treatment.
Only 12 hours after an egg cell is fertilized by a sperm cell, the egg cell starts to divide. As it continues to divide, it moves along the fallopian tube toward the uterus at about 1 inch per day.