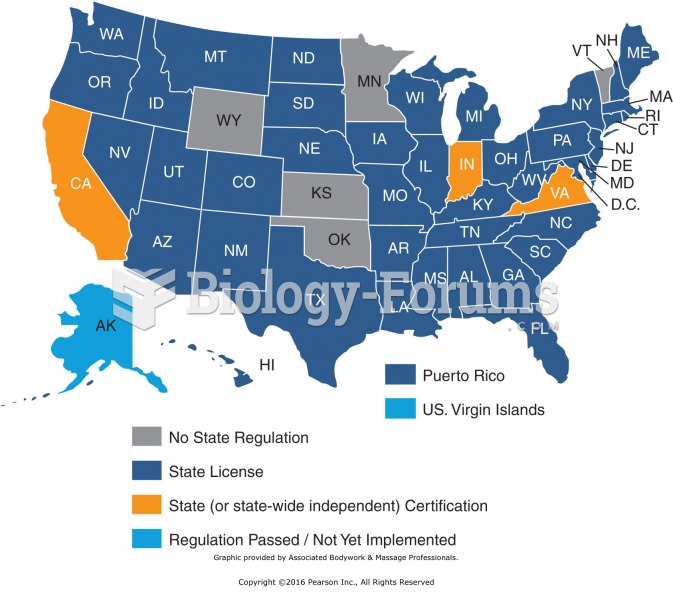
|
|
|
Did you know?
Automated pill dispensing systems have alarms to alert patients when the correct dosing time has arrived. Most systems work with many varieties of medications, so patients who are taking a variety of drugs can still be in control of their dose regimen.
Did you know?
Cucumber slices relieve headaches by tightening blood vessels, reducing blood flow to the area, and relieving pressure.
Did you know?
On average, someone in the United States has a stroke about every 40 seconds. This is about 795,000 people per year.
Did you know?
Pubic lice (crabs) are usually spread through sexual contact. You cannot catch them by using a public toilet.
Did you know?
Earwax has antimicrobial properties that reduce the viability of bacteria and fungus in the human ear.