|
|
|
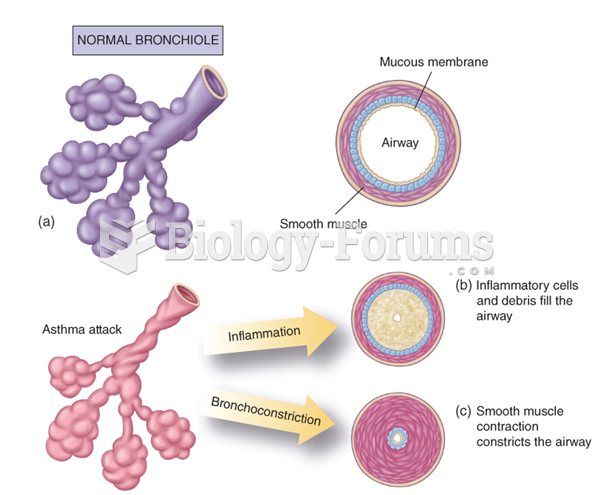
Asthma occurs in one in 11 children and in one in 12 adults. African Americans and Latinos have a higher risk for developing asthma than other groups.
In 2012, nearly 24 milliion Americans, aged 12 and older, had abused an illicit drug, according to the National Institute on Drug Abuse (NIDA).
Intradermal injections are somewhat difficult to correctly administer because the skin layers are so thin that it is easy to accidentally punch through to the deeper subcutaneous layer.
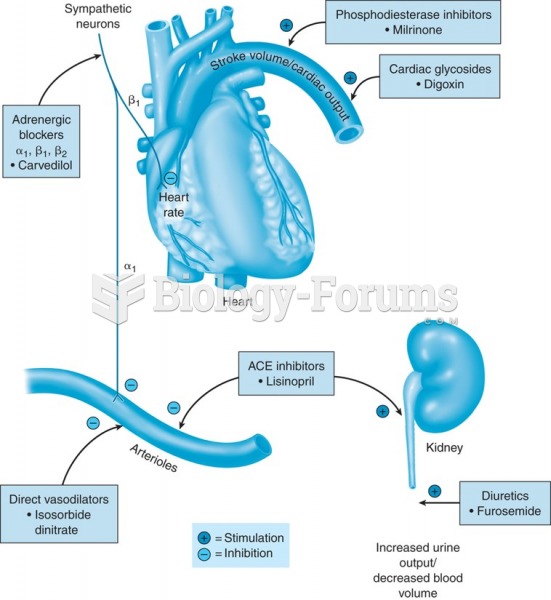
Congestive heart failure is a serious disorder that carries a reduced life expectancy. Heart failure is usually a chronic illness, and it may worsen with infection or other physical stressors.
Inotropic therapy does not have a role in the treatment of most heart failure patients. These drugs can make patients feel and function better but usually do not lengthen the predicted length of their lives.