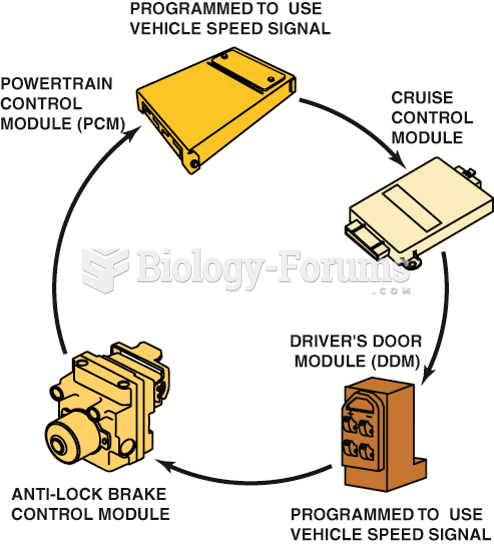
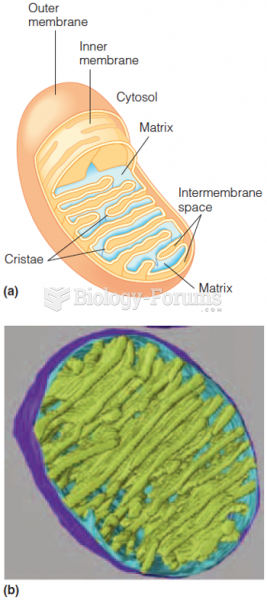
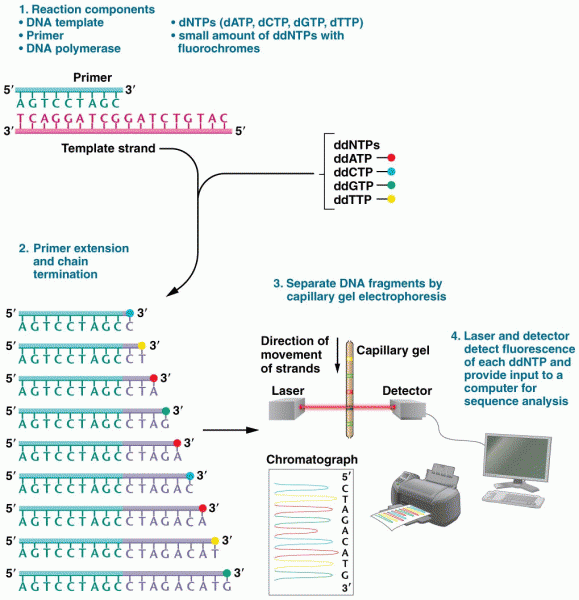
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
There are more bacteria in your mouth than there are people in the world.
Did you know?
When intravenous medications are involved in adverse drug events, their harmful effects may occur more rapidly, and be more severe than errors with oral medications. This is due to the direct administration into the bloodstream.
Did you know?
Urine turns bright yellow if larger than normal amounts of certain substances are consumed; one of these substances is asparagus.
Did you know?
Elderly adults are living longer, and causes of death are shifting. At the same time, autopsy rates are at or near their lowest in history.
Did you know?
The ratio of hydrogen atoms to oxygen in water (H2O) is 2:1.
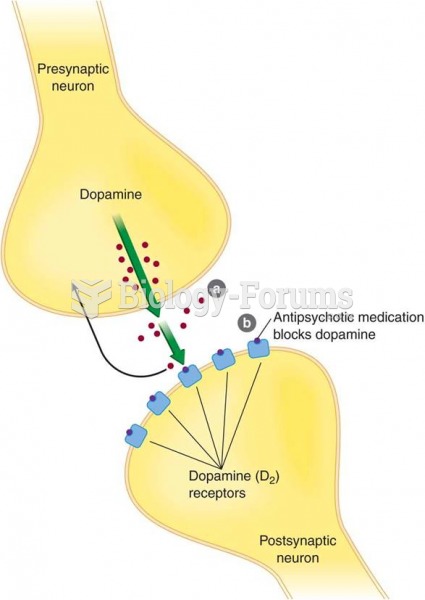 Mechanism of action of antipsychotic drugs: (a) overproduction of dopamine; (b) antipsychotic medica
Mechanism of action of antipsychotic drugs: (a) overproduction of dopamine; (b) antipsychotic medica
 Children in Baltimore (1909) pull the stringy parts from beans in preparation for canning. Photograp
Children in Baltimore (1909) pull the stringy parts from beans in preparation for canning. Photograp
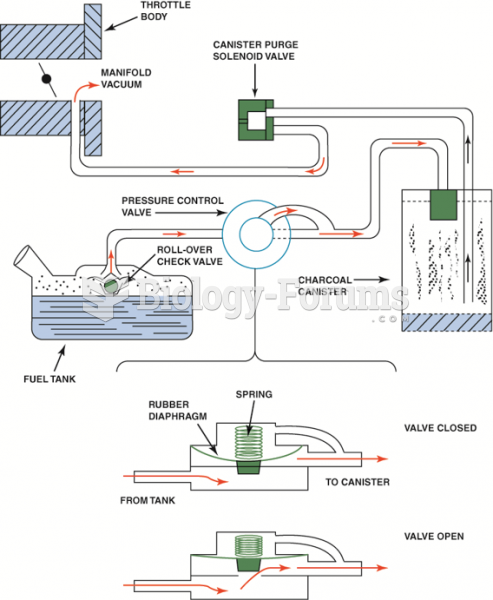 A typical evaporative emission control system. Note that when the computer turns on the canister ...
A typical evaporative emission control system. Note that when the computer turns on the canister ...