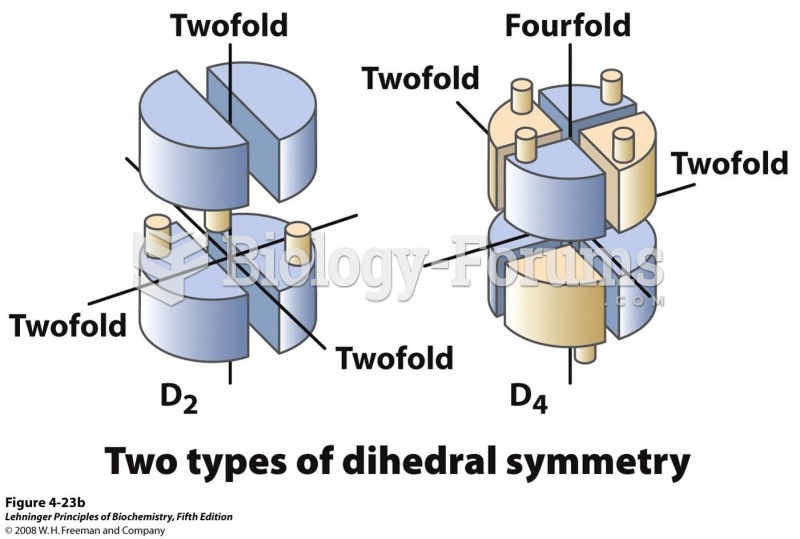
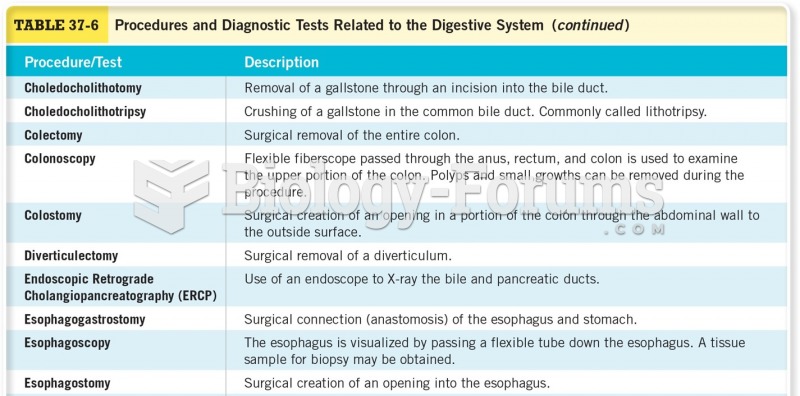
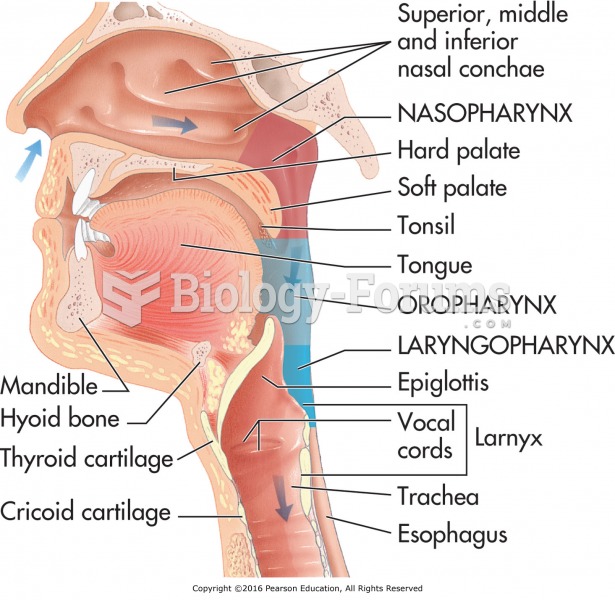
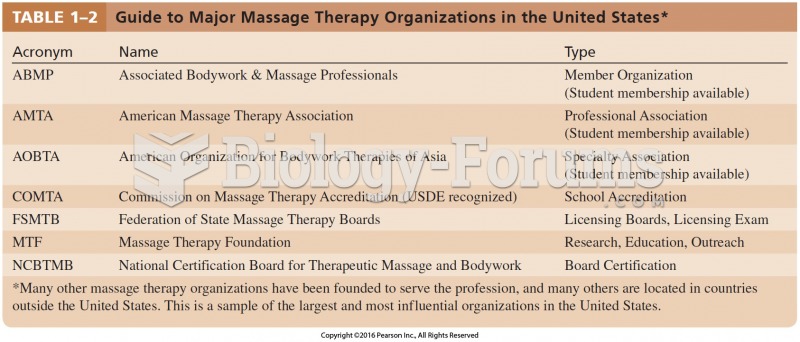
|
|
|
The first successful kidney transplant was performed in 1954 and occurred in Boston. A kidney from an identical twin was transplanted into his dying brother's body and was not rejected because it did not appear foreign to his body.
The human body produces and destroys 15 million blood cells every second.
The first-known contraceptive was crocodile dung, used in Egypt in 2000 BC. Condoms were also reportedly used, made of animal bladders or intestines.
The first oral chemotherapy drug for colon cancer was approved by FDA in 2001.
The Centers for Disease Control and Prevention has released reports detailing the deaths of infants (younger than 1 year of age) who died after being given cold and cough medications. This underscores the importance of educating parents that children younger than 2 years of age should never be given over-the-counter cold and cough medications without consulting their physicians.