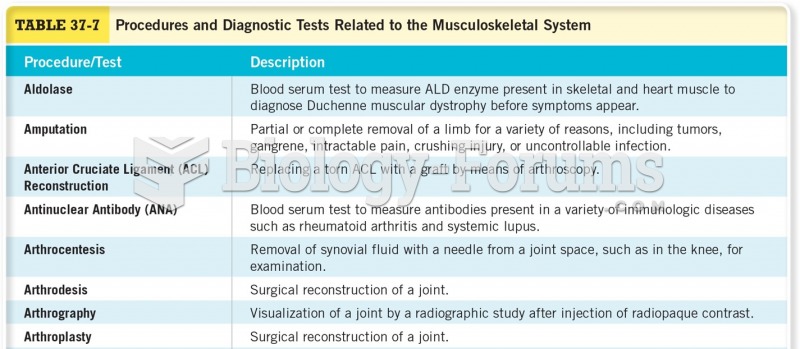
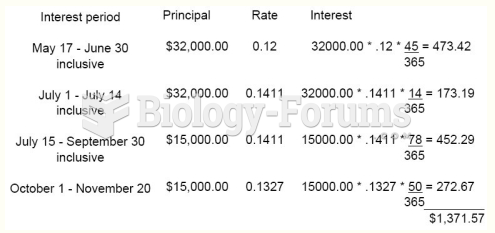
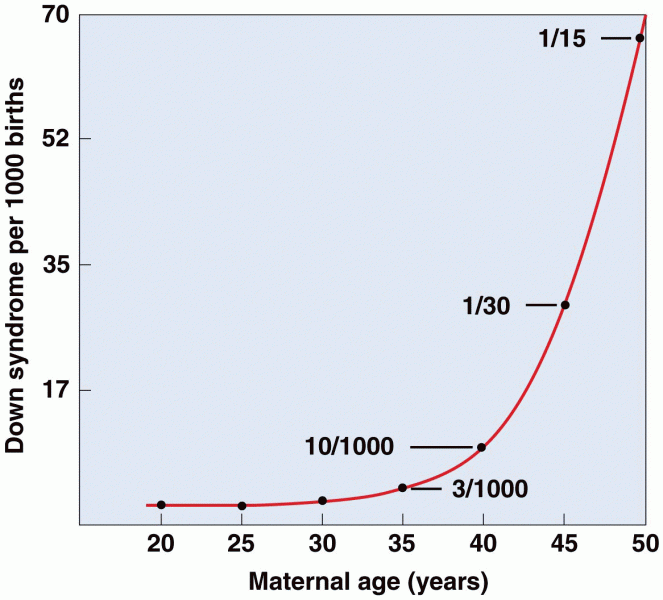
|
|
|
About 60% of newborn infants in the United States are jaundiced; that is, they look yellow. Kernicterus is a form of brain damage caused by excessive jaundice. When babies begin to be affected by excessive jaundice and begin to have brain damage, they become excessively lethargic.
Human kidneys will clean about 1 million gallons of blood in an average lifetime.
People about to have surgery must tell their health care providers about all supplements they take.
In ancient Rome, many of the richer people in the population had lead-induced gout. The reason for this is unclear. Lead poisoning has also been linked to madness.
Essential fatty acids have been shown to be effective against ulcers, asthma, dental cavities, and skin disorders such as acne.