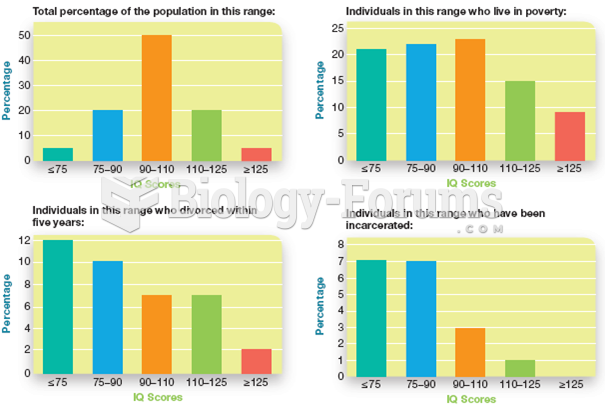
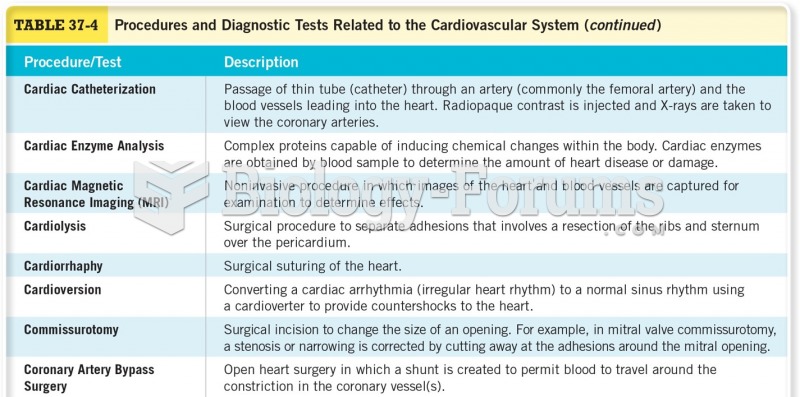
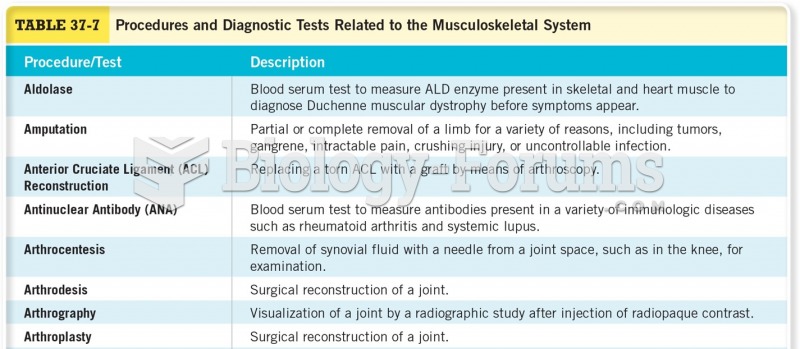
|
|
|
The top five reasons that children stay home from school are as follows: colds, stomach flu (gastroenteritis), ear infection (otitis media), pink eye (conjunctivitis), and sore throat.
Though the United States has largely rejected the metric system, it is used for currency, as in 100 pennies = 1 dollar. Previously, the British currency system was used, with measurements such as 12 pence to the shilling, and 20 shillings to the pound.
The average human gut is home to perhaps 500 to 1,000 different species of bacteria.
According to the National Institute of Environmental Health Sciences, lung disease is the third leading killer in the United States, responsible for one in seven deaths. It is the leading cause of death among infants under the age of one year.
The National Institutes of Health have supported research into acupuncture. This has shown that acupuncture significantly reduced pain associated with osteoarthritis of the knee, when used as a complement to conventional therapies.