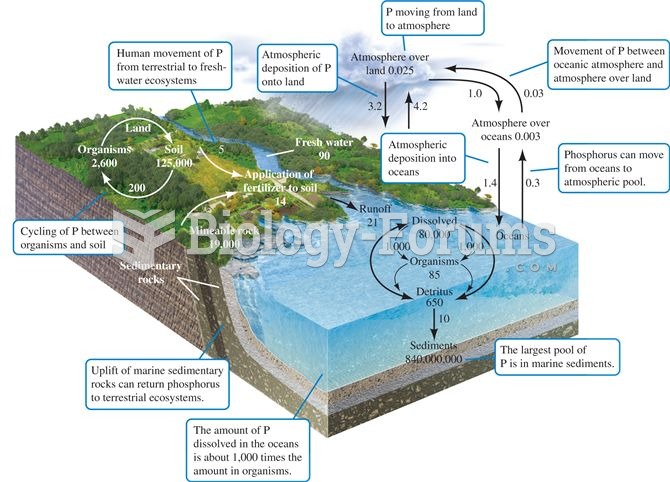
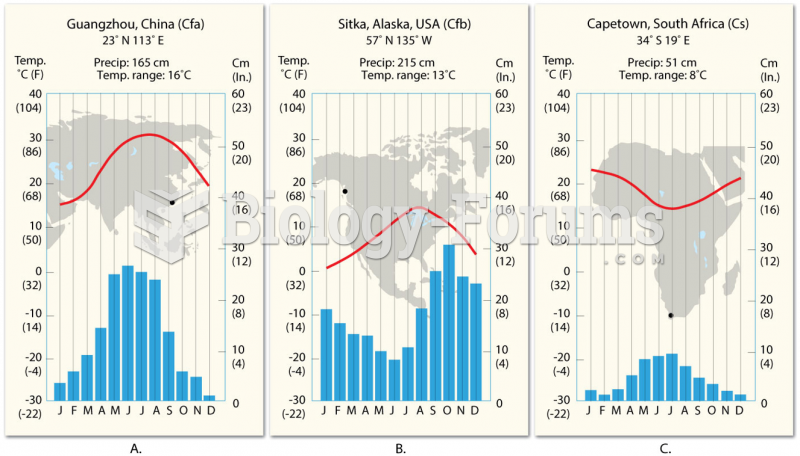
|
|
|
Blood in the urine can be a sign of a kidney stone, glomerulonephritis, or other kidney problems.
The liver is the only organ that has the ability to regenerate itself after certain types of damage. As much as 25% of the liver can be removed, and it will still regenerate back to its original shape and size. However, the liver cannot regenerate after severe damage caused by alcohol.
Autoimmune diseases occur when the immune system destroys its own healthy tissues. When this occurs, white blood cells cannot distinguish between pathogens and normal cells.
More than 34,000 trademarked medication names and more than 10,000 generic medication names are in use in the United States.
Cocaine was isolated in 1860 and first used as a local anesthetic in 1884. Its first clinical use was by Sigmund Freud to wean a patient from morphine addiction. The fictional character Sherlock Holmes was supposed to be addicted to cocaine by injection.