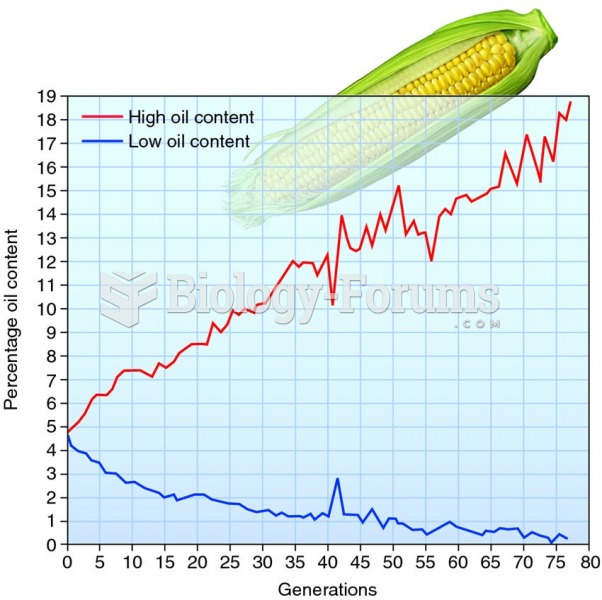
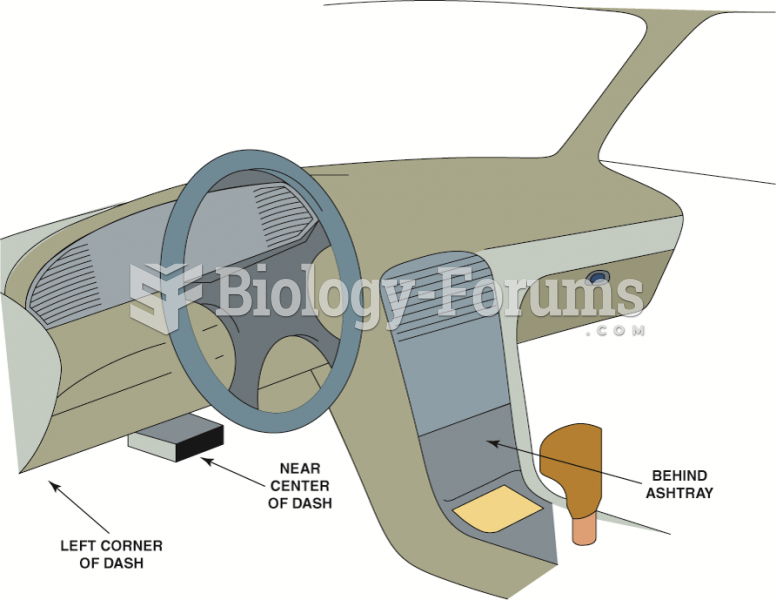
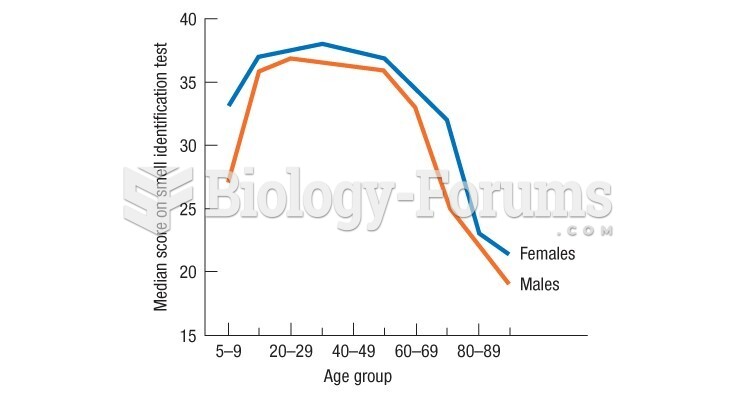
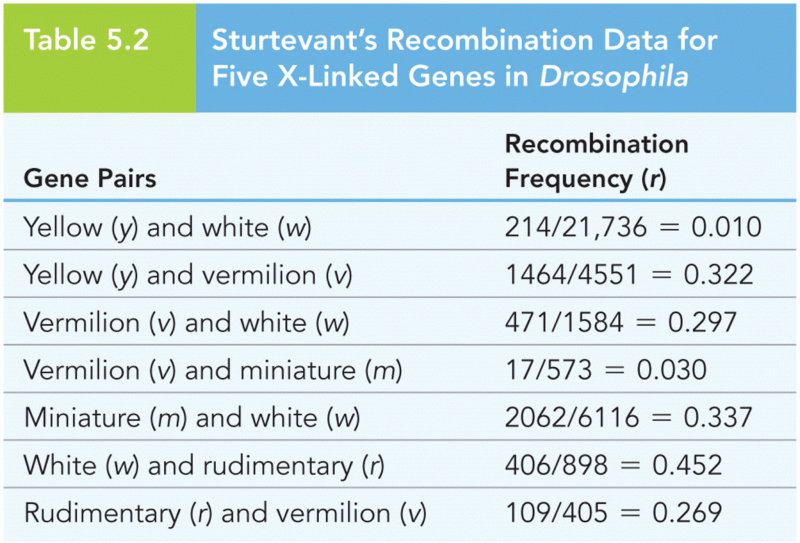
|
|
|
Amoebae are the simplest type of protozoans, and are characterized by a feeding and dividing trophozoite stage that moves by temporary extensions called pseudopodia or false feet.
Hip fractures are the most serious consequences of osteoporosis. The incidence of hip fractures increases with each decade among patients in their 60s to patients in their 90s for both women and men of all populations. Men and women older than 80 years of age show the highest incidence of hip fractures.
Drying your hands with a paper towel will reduce the bacterial count on your hands by 45–60%.
In 1844, Charles Goodyear obtained the first patent for a rubber condom.
People with alcoholism are at a much greater risk of malnutrition than are other people and usually exhibit low levels of most vitamins (especially folic acid). This is because alcohol often takes the place of 50% of their daily intake of calories, with little nutritional value contained in it.