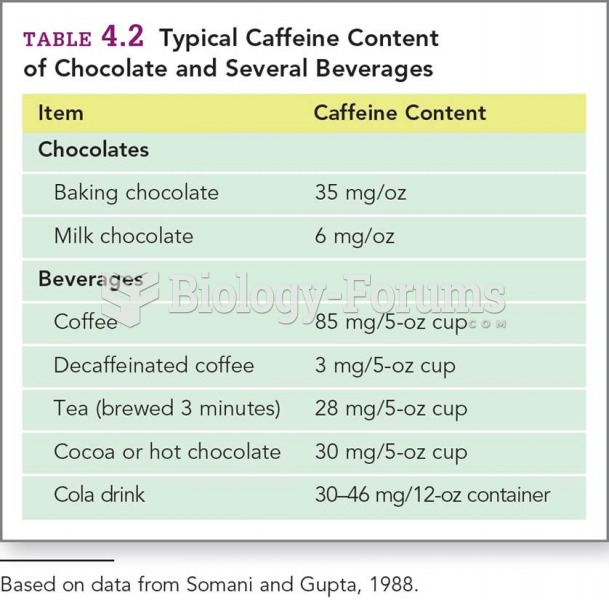
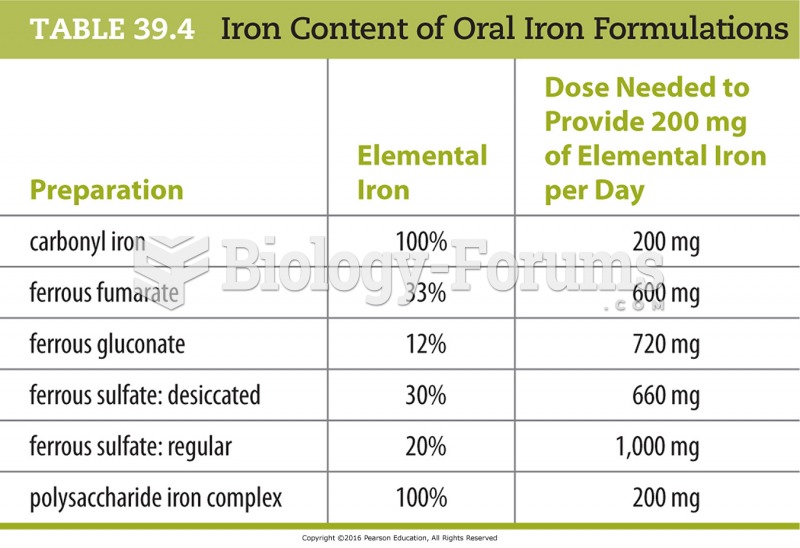
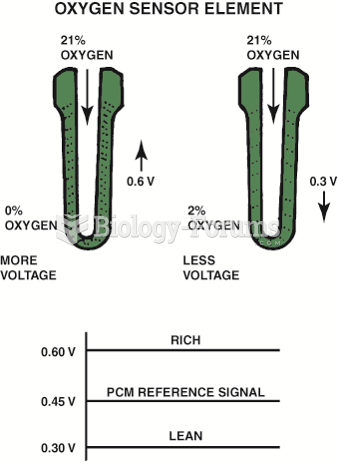
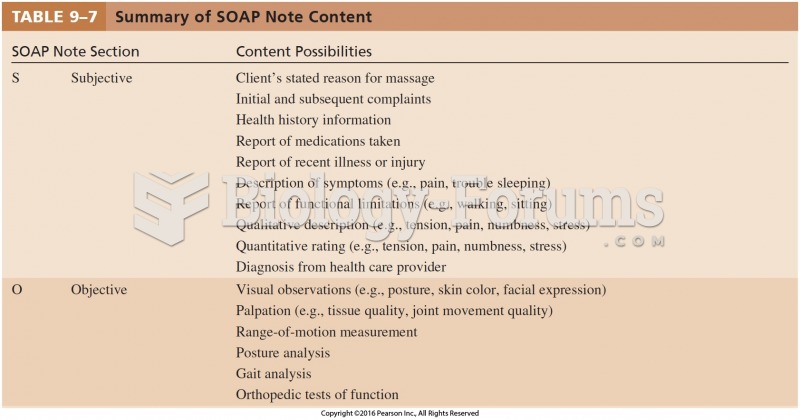
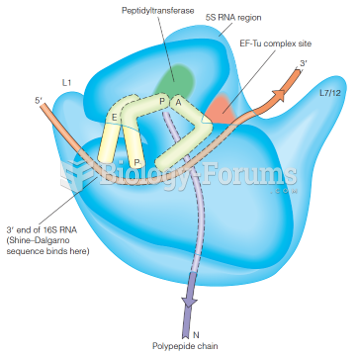
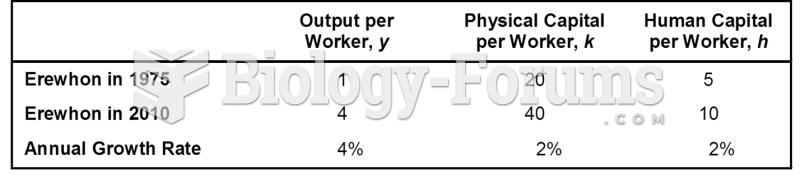|
|
|
Hypertension is a silent killer because it is deadly and has no significant early symptoms. The danger from hypertension is the extra load on the heart, which can lead to hypertensive heart disease and kidney damage. This occurs without any major symptoms until the high blood pressure becomes extreme. Regular blood pressure checks are an important method of catching hypertension before it can kill you.
Asthma-like symptoms were first recorded about 3,500 years ago in Egypt. The first manuscript specifically written about asthma was in the year 1190, describing a condition characterized by sudden breathlessness. The treatments listed in this manuscript include chicken soup, herbs, and sexual abstinence.
The types of cancer that alpha interferons are used to treat include hairy cell leukemia, melanoma, follicular non-Hodgkin's lymphoma, and AIDS-related Kaposi's sarcoma.
Critical care patients are twice as likely to receive the wrong medication. Of these errors, 20% are life-threatening, and 42% require additional life-sustaining treatments.
About 600,000 particles of skin are shed every hour by each human. If you live to age 70 years, you have shed 105 pounds of dead skin.