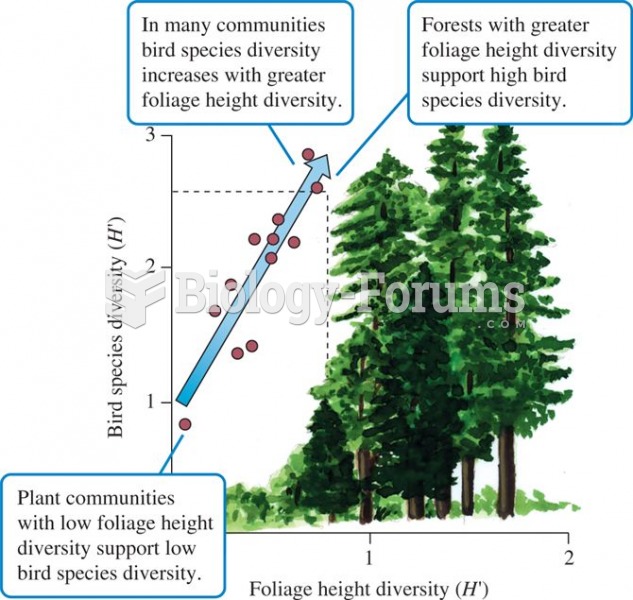
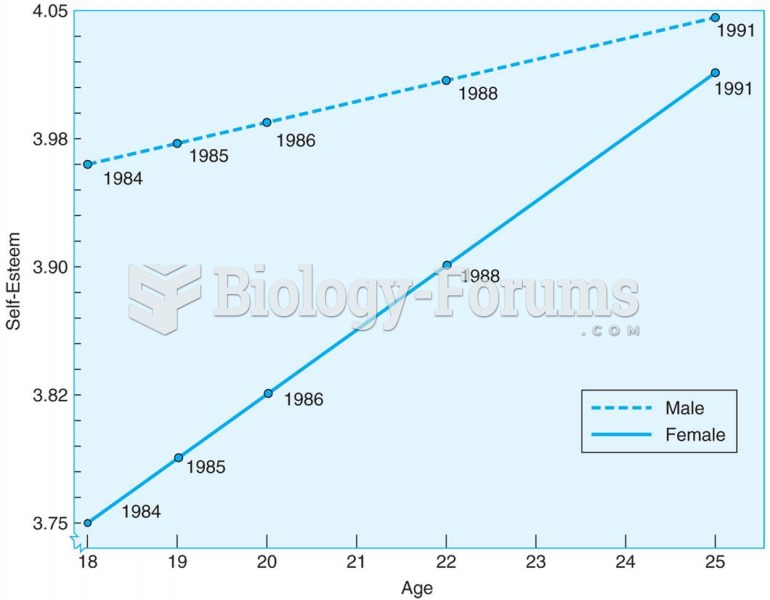
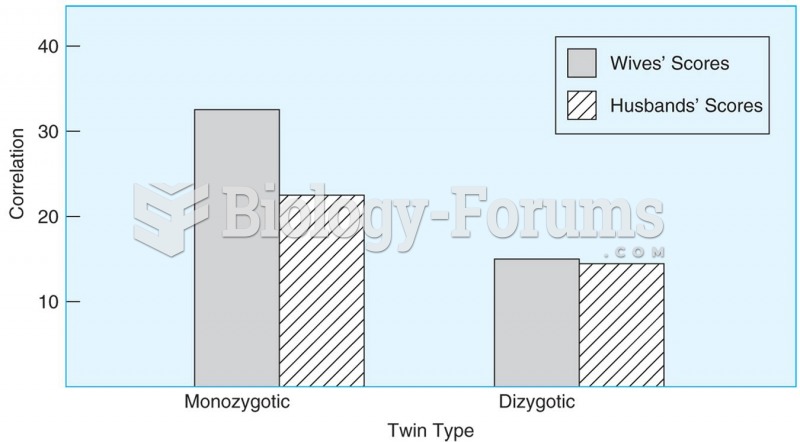
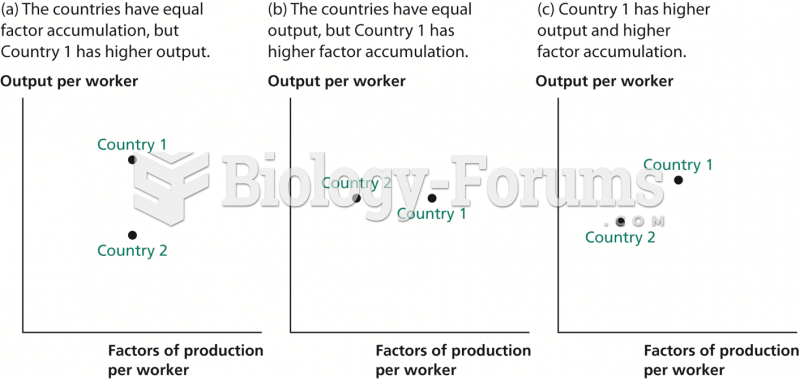
|
|
|
A recent study has found that following a diet rich in berries may slow down the aging process of the brain. This diet apparently helps to keep dopamine levels much higher than are seen in normal individuals who do not eat berries as a regular part of their diet as they enter their later years.
Nearly all drugs pass into human breast milk. How often a drug is taken influences the amount of drug that will pass into the milk. Medications taken 30 to 60 minutes before breastfeeding are likely to be at peak blood levels when the baby is nursing.
One way to reduce acid reflux is to lose two or three pounds. Most people lose weight in the belly area first when they increase exercise, meaning that heartburn can be reduced quickly by this method.
The eye muscles are the most active muscles in the whole body. The external muscles that move the eyes are the strongest muscles in the human body for the job they have to do. They are 100 times more powerful than they need to be.
Computer programs are available that crosscheck a new drug's possible trade name with all other trade names currently available. These programs detect dangerous similarities between names and alert the manufacturer of the drug.